Why You Should Use A VPN
Internet, Safety And You
The Internet is crazy big. Believe it or not it is just about everywhere on the planet. The Internet of Things makes it so, there are smart devices of all variety filled with sensors and microprocessors sending and receiving data around the clock. The problem is that the Internet is also very much like the Wild West, where anything goes if you can get away with it. This makes safety a top priority when using it. You need to be safe for the health of your devices, you need to protect your connections while using the Internet and you need to protect the safety of your data because all are at risk.
- There are estimated to be well over 100,000 known active Internet Viruses. Symantec has claimed to protect against more than 1 million.
- There are estimated to be more than 6.5 million websites, the number fluctuates rapidly, the average life of a website is about 90 days.
Hackers and malware are only one concern. Threats exist in more mundane places as well, such as with an eCommerce website, where information about you, your devices or location may be stored. A foolproof security system at home does you no good if your information is leaked by someone you thought you could trust, or if your connection with their website leaves you exposed. Considering the sheer size of the Internet of Things that means there are dozens, hundreds, thousands of potential avenues through which harm can be done to you, your family, your devices, your home or your business.
Firewalls and malware protection are important tools in the fight to keep you safe. They block potentially harmful websites and software from accessing your machines, they prevent the installation of unwanted viruses and spyware but they don't give 100% protection. Your IP address is still getting blasted across the web, your connections are still visible and your devices are still traceable. The only way to protect yourself fully is to use a VPN, only most people have never heard of one.
What Is A VPN?
VPN, Virtual Private Network, has been around almost as long as the Internet itself. To understand how it works let me start at the beginning. The Internet is not a physical thing, it is a method and a protocol dictating how the locations of physical devices are to be labeled so that routers can direct traffic appropriately. You see, computer networks existed before the Internet. They belonged to large corporations, governments and anyone else with the money and tech savvy to create one. The Inter-Net is the method by which these disparate networks were tied together. Now that computers and smart devices with web surfing capabilities are so commonplace it has grown to include individuals and devices.
- VPN was created to allow remote users such as branch offices, satellite employees or business travelers to connect securely to their home network using the public Internet. One of the technological break-through's that allow the Internet and VPN to function is the packetization of data.
Think about this, the original phone lines were a direct connection. That means when you called someone up your phone was connected directly to their phone through a switch board and then your conversation flowed freely across that line, available to anyone tied into it. Packetization means that the data does not flow freely and directly across the lines, it is bundled and formed into packets which are labeled with IP ADDRESSES and other identifying information and then routed to the end point where it is unbundled and delivered. Routers use the IP information to direct the flow of data across whatever lines are available. The bad news is, like I mentioned before, all this identifying information is available for viewing by anyone and any device with interest and ability.
The VPN is actually a combination of several technologies developed through private sector and government/military funded research. It uses encryption, re-packeting, secure routing and end-point authentications to establish point-to-point connections that are virtually impossible to detect, extremely unlikely to be followed and if intercepted, so time and money consuming to decipher no one will ever try.
What happens is this. The VPN software will be included inside the Payload portion of your data packets. When the packet is ready to be sent, it (the VPN) will work from inside to encrypt the data, creating an undetectable shield. It will also encrypt the IP information but more importantly, it will create a new data packet which includes the entire original packet, only with a new IP address from the dedicated VPN server, so that it is encrypted and ANONYMOUS to random viewers. The new packet is then routed through said server, bypassing your ISP and traditional avenues of deliver, in a fully encrypted and untraceable manner. When it emerges, which only happens at the endpoint, it must first authenticate the recipient before it will decrypt for use.
Providers like Le VPN have servers located around the world that function on several specific VPN protocols, each offering different levels of security and advantages for Internet users. Once you download the software (the software does the encrypting and repacketing of data, before the connection is made, to ensure total privacy and security) all you have to do is click on which server you want to connect to, just as if you were logging into your local Internet access provider.
How To Protect Your Data Online
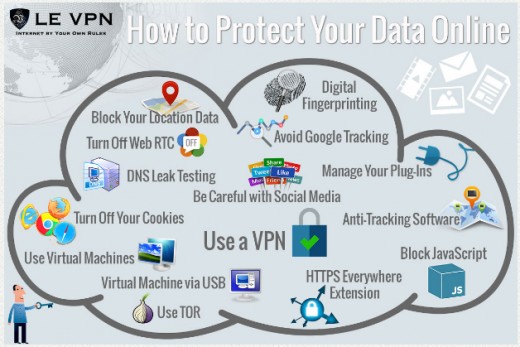
Common Uses For VPN
- Total Home Security - Connect all home/local devices through the VPN to keep physical and LAN information safe from hackers and malware.
- Avoiding Geo-restrictions - One benefit of VPN and remote servers is that your geo-location and IP addresses are masked. This allows users to unlock geo-restricted content such as the majority of US streaming TV from ABC, NBC, CBS and all the rest, the BBC's UK only streaming website, YouTube, social media and much much more. For those living in heavily censored countries VPN can keep you safe from censors and other unwanted invasions of privacy.
- Connecting Over A Wi-Fi HotSpot - WiFi hotspots are prime targets for hackers. Hotspots in Airports, coffee shops, fast food restaurants and anywhere else where a free connection can be established are also places where digital eavesdropping is easiest to do. Connections are made over a public available interface and can be readily intercepted. VPN's create a safe, secure connection alleviating this risk.
- Evade Internet Throttling - Many Internet providers will control the amount of data your connections will allow to flow at one time. They do this to reduce the impact on their services and to create different price points for those same services. Websites like YouTube and popular online first-person-shooter games like Black Ops are obvious examples. Movies can take a long time to buffer, games can have pauses or worse. VPN will hide your connection even from your ISP and prevent this from happening.
- Avoiding Data Collection -Every website collects some kind of information about you. Website like Google and Facebook collect every piece of information about you they can, and then share it among their many apps and partners in order to "enhance" your experience and these are innocent examples. Other, less innocent, data collection is going on as well and VPN will prevent it from happening too.
How Good Is Le VPN?
Different VPN Protocols For Different Needs
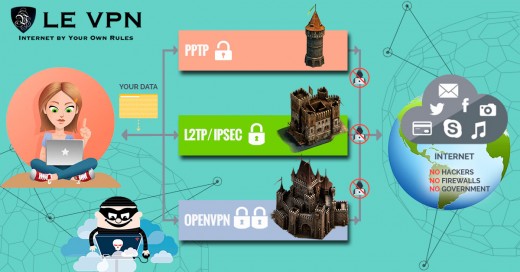
Le VPN - VPN Protocols
Protocol
| ||
|---|---|---|
PPTP
| Most commonly used, easy to set up, encrypted, great for general web surfing
| $4.95 month/1 Year Plan
|
L2TP/IPSEC
| Advanced PPTP, encrypted, multi-authentication process. Best for transmitting sensitive information.
| included
|
Open VPN
| Open source VPN using SSL connections to bypass firewalls and ISP restrictions. Best for sending sensitive information.
| included
|
Hybrid VPN
| Combines SSL VPN with Smart DNS proxy, best for unlocking geo-restricted TV
| included
|
VPN For Mobile
| Android, iOS
| included
|
You Already Use VPN Technology, You Just Don't Know It
VPN's do exist in our everyday lives, even if you yourself take advantage of a personal VPN. SSL and HTTPS are two common uses of the VPN technology that websites and businesses uses every day to ensure the safety of their corporate networks as well as that of their customers.
- SSL, Secure Socket Layer, is a point-to-point tunneling protocol and the standard for establishing an encrypted connection between a website and a web browser. They are used for things like filling out forms, eCommerce checkout and online banking.
- HTTPS is the more advanced and secure version of the old standard HTTP. It's appearance in your address bar means that all traffic between you and the website is encrypted.
These two applications are incredibly helpful in controlling misuse of the Internet but remain vulnerable to attacks that a personal VPN can protect you from.
How VPN Works, The Basics
Complete Internet Security
I think it is safe to say that Internet is here to stay. It is one of if not the most influential developments in modern technology; it connects the world together and puts power at the fingertips of even the most novice of users. I also think it is safe to say that internet frauds/scams, data mining, eavesdropping, geo-restrictions, hacking and malware are also here to stay. The appeal and applications are just too great, the minds of devious people too cunning, to prevent these intrusions of privacy from happening. This means Internet security is a must. Firewalls, malware, email/websurfing best practices and above all a VPN are requirements for ensuring your safety and your privacy.