Different Kinds of Malware and Spyware and Viruses
Different Kinds of Malware and Spyware and Viruses
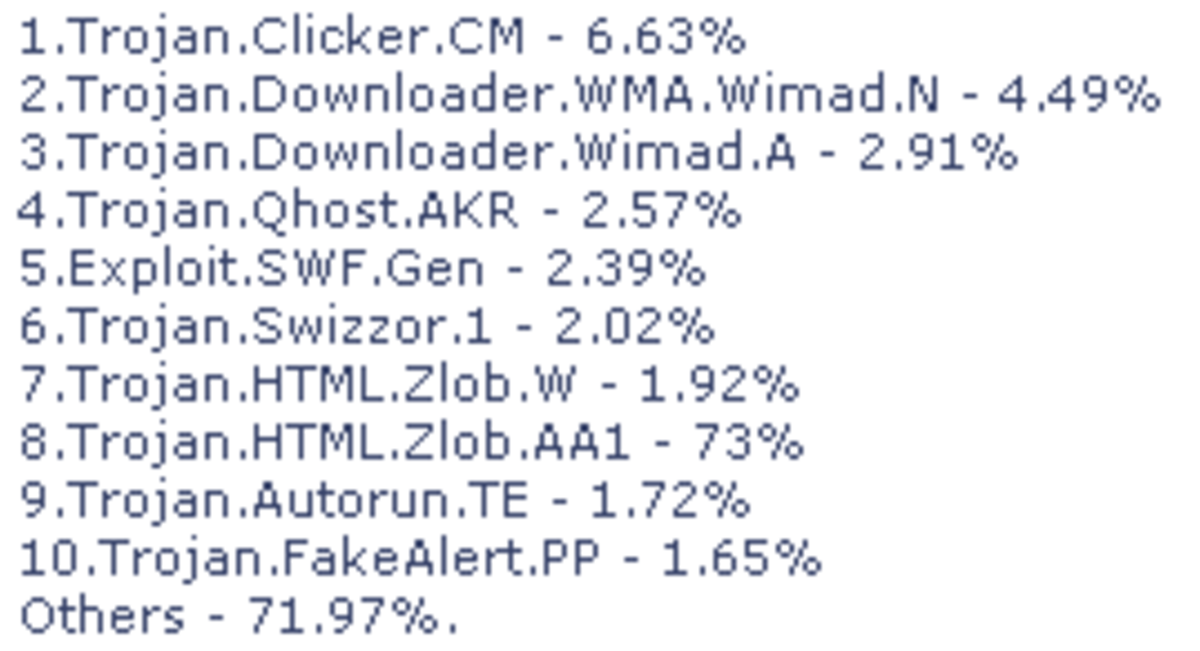
The high-tech world of computing presents multiple challenges such as how much RAM to purchase, what operating system to install, and how to avoid malware, spyware, and viruses. Herein we present a brief compendium of nasty software that hardly anyone wants on their computer. Read on to learn about several different kinds of programs causing mass problems in the universe of digital happenings.
Malware
Malware is a category of software programs that negatively impact the operation of your computer and are typically installed without your consent. Devious computer programmers create programs to do evil things such as:
- Capture your keystrokes and relay them to a remote computer,
- Monitor your Internet browsing activity and insert relevant advertising windows to sell you stuff,
- Use your Internet connection to send spam email to unsuspecting recipients,
- Store files on your computer for other people around the world to access, and
- Steal your files for the purpose of obtaining personal information about you.
The simplest (and only) way to keep a computer 100% secure is to never connect it to the Internet. Short of that, knowledge is power. "Know your malware" should be the mantra of every computer user from Sacramento to Schenectady.
What kinds of Malware Threatens Your Computer?
Malware variants proliferate virtually every day, but a few obvious strains should be familiar to responsible computer users. Here are a few things to look for.

Foulware
Overview: Your computer becomes part of an Intranet connecting hen houses throughout Iowa and Indiana.
Symptoms:
- Internet browser refuses to load chickfila.com.
- Screen Saver changes to an advertisement for EggLand's Best.
Residue: Look for cLuCk.dll in in your Program Files folder.
Removal: Go outside and play. Wash your car. Introduce yourself to your neighbors.
=======================================
Palware
Overview: Your computer becomes part of an international social network interconnecting millions of user who otherwise would be able lead normal lives. Your twitter account fills up with messages from people you've never heard of who insist on telling the world how long the line might be at the local Starbucks.
Symptoms: Hundreds of new icons appear in your taskbar for each of the social networking apps installed on your computer. Everyone in the world seems to know what you're doing before you do.
Residue: Scan your My Documents folder for text files exactly 140 characters long.
Removal: Go outside and play. Buy a Frisbee, mow the lawn, take up fishing.
=======================================
Cowlware
Overview: Your computer becomes part of the Gotham City emergency response network.
Symptoms: When crime rears its' ugly head, your screen saver becomes a Bat Signal. Any attempt to play online poker results in nothing but jokers.
Residue: Look for registry entry [HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\AU\riddlerEnabled].
Removal: Go outside and play. Learn to play tennis. Borrow a kayak. Rake your leaves.
=======================================
Owlware
Overview: Your computer becomes a mouse server for raptor birds in your neighborhood.
Symptoms:Your Internet browser pops up ads for hamster accessories. You begin receiving unsolicited emails from the Sierra Club.
Residue: Mouse droppings in the power supply will no longer be a problem.
Removal: Go outside and play. Count the stars in the sky. Sweep your driveway.
=======================================
Conclusion
Be painfully aware of different kinds of malware and spyware and viruses and how they might infest your computer.