Heartbleed Bug Leaves Internet Users Open To Being Hacked

What is OpenSSL?
OpenSSL is the most common web encryption program on the internet that users only recognize by seeing HTTPS or a padlock in their top left corner of their screen, telling them that the website is secure. Rarely do they know it by its OpenSSL name.
Privacy notices spell it out, but you - the average user - have no idea how it functions and many don't even take the time to read those privacy notices or Terms of Service.
Check screenshots below to test the sites you use most often.
Tumblr's warning to users
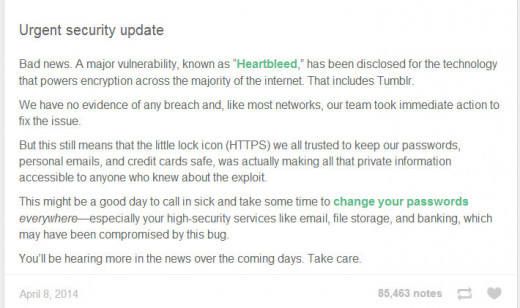
It is a big deal, no matter if you hear differently!
On Monday, April 8, 2014, trillions of passwords, credit card numbers and other personal information became attractive to hackers when Google's security team learned a bug named HEARTBLEED could access the web encrypted program known as OpenSSL.
It doesn't mean that hackers did access it. What it means is that there is no way to know if they did.
This bug reads the web encrypted program OpenSSL which many websites use to store your private information, passwords, file storage websites, bank and credit cards, as well as your private online conversations - anything this is encrypted with the padlock or HTTPS in top left of your screen.
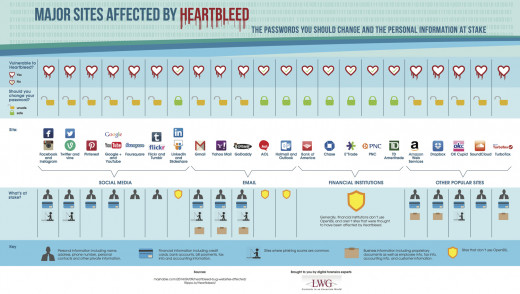
The HEARTBLEED bug is a flaw affecting 66% of websites on the internet who use OpenSSL web encryption programs to protect the privacy of its users.
The HEARTBLEED bug allows anyone on the Internet to read the memory of the systems protected by the vulnerable versions of the OpenSSL software.
This compromises the secret keys that are used to identify the service providers and to encrypt the traffic, users names and their passwords as well as their private content.
The HEARTBLEED bug is an eavesdropper which allows hackers to steal directly from the servers as well as the users so they can go on to impersonate or even steal the identity of each user.
There are always going to be bugs in software and software libraries and there are always going to be patches or new versions introduced. You see this every day when you are upgrading a program or new version of a game, for example.
But the HEARTBLEED bug is rather unique because this bug exposes a large number of private keys to anyone on the internet who is monitoring a site. When you consider the long range exposure (now over two years!), how easy it is to access and attack while leaving no trace behind, this bug should be taken very seriously!
Although a patch has been offered to websites and servers to address their vulnerability, the level of importance this has received has not made them act quickly.
This is partly because the level of the breach was not given a high priority.
Researchers hesitated to call it a virus or even malware. They are calling it a bug at this point because it is a nuisance program that steals information, but does not do any residual damage to your computer as would a virus or malware.
In other words, it does not leave behind adware or malware, so the level of importance assigned to it is low.
Make no mistake about it -- this IS a very big deal.
It is a major breakdown in internet security and the trust level on any site using any type of WoT (Web of Trust) program even if they don't use this version of OpenSSL.
Once any security program or website server has been breached, it reflects on all security programs, because you can't change the public's perception of how secure they feel about their online information.
Anything that attacks or accesses our private information - or information we deem to be private - is a big deal to us, even if the powers that be don't think so.
See screenshots below with link to test your favorite sites to see if they applied the patch (fix). If their grade is not A or higher, I wouldn't change the passwords just yet.
HEARTBLEED bug Update 4/16/2014
Hubpages.com
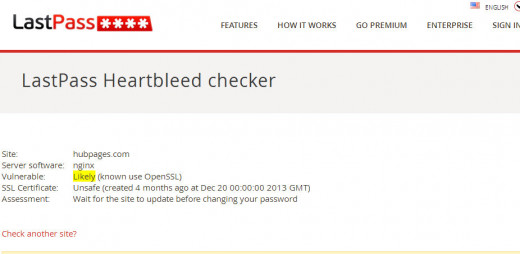
Update: 4/10/2014 - 6pm Est
Matthew Meyer suggested this link to check Hubpages for site health with HEARTBLEED
It gets an all clear!
Test your secure websites and see how secure they are with this tool
Use this link to see if your domain, website, server is affected. After the first screen, wait 30 seconds, it will give you a second screen with a grade and key exchange. If it says "confusing" just hold on for 30 seconds because the screen is still working and it will give you the second screen. If the results on the first screen give a grade less than A, it is not the final answer because it is a working screen - a screen that gives you a bit of information before it goes on to give you more information on subsequent screens - so hang on for 30 seconds.
Hubpages.com came up "confusing" and while I was entering it in heartbleed.com to see what that site offered, when I came back to Qualys SSL screen, it had given hubpages.com an all clear. heartbleed.com is faster but doesn't give the detailed information that this site does.
So that is what I have to suggest between Qualys SSL screen and heartbleed.com screens.
Keep it bookmarked and go back often to check by entering the URL.
This is a free online service that analyzes any SSL web server on the internet, not just OpenSSL.
If you can't click it, here it is for you to copy and paste it into your browser.
https://www.ssllabs.com/ssltest/index.html
SEE SCREENSHOTS
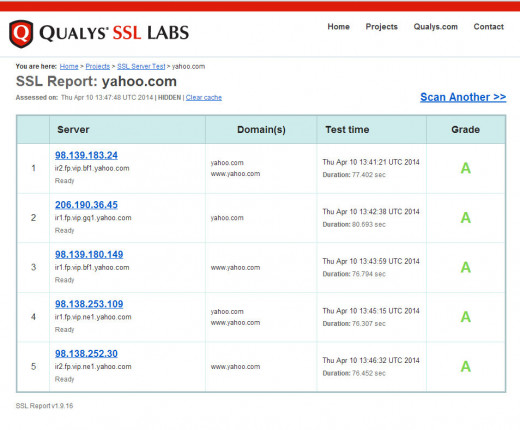
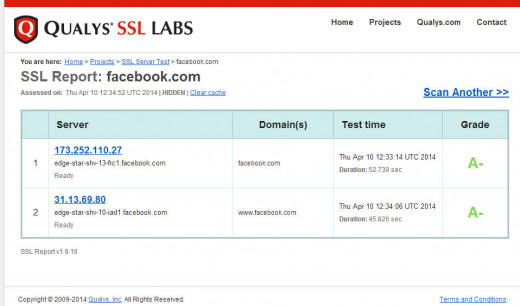
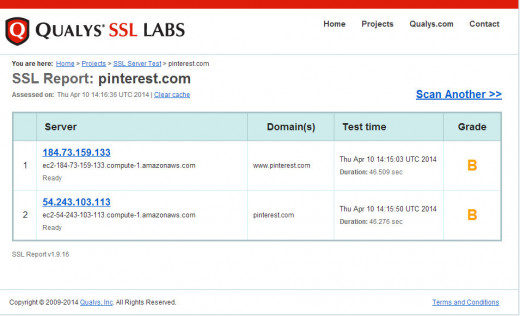
Screenshots of SSL Server Test (I tested Pinterest, Facebook, Yahoo)
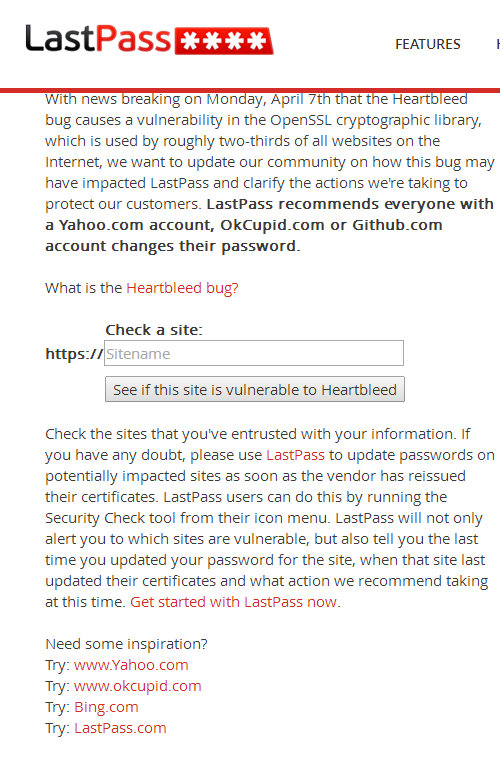
LastPass Instructions
LastPass is another site to use. The screenshot below is only to show you what the landing page looks like. Do not try to enter information on the screenshot.
Click the link under the screen shot or copy and paste this link into your browser.
https://lastpass.com/heartbleed/
Do not click anything else on the site when you get there. It has a download to install a checker on your computer. It also has a Premium set of services that you have to pay for. Just use the Site checker.
You don't need it. Using the free section of their website is good enough!
Use The Last Pass Checker (just check, don't download anything!)
Notifying the public
Today is Thursday, April 10, 2014 and we are still talking about more than half the affected sites who have not hurried to install the fix.
The damage caused by the HEARTBLEED bug is unknown at this point. The irony is this encryption program has been in use for over two years on millions of websites to safeguard private information, the security hole has been there that long, but the bug has just been discovered on Monday, April 8, 2014.
It is possible that the vulnerability has not yet been detected by hackers, because there have been no reports of a hack or major breach reported by credit card companies or bank, but that doesn't mean there might not be one in the offing.
Any website or server who encrypts data would do well to err on the side of caution and install the patch to heal the vulnerability. (Hint to any web administrator reading this!)
Now that the word is out that the bug has been discovered, it won't be long before hackers practice their trade to see if they can be successful in cracking the bug and/or the patch fixes to send in a virus to attack the bug.
One never knows the repercussions of alerting the public to incidents like HEARTBLEED bug, when it could leave the door open for hackers to take advantage of the same public service announcement and try their hand at making a bad situation even worse by actually doing the dirty deed of stealing the information, thus bringing about the worse fears when the bug was announced in the first place.
If it was a possibility of stealing information on Monday, by now hackers have found a way to make it a reality.
The privacy notices on websites will now have to be revamped and retooled to assure users that their information is safe. It is times like these that we have to wonder.
All you know is that they are assuring you that your safety is their highest priority and that your information is safe with them.
Trust me, it is never going to be 100% safe.
Even with the padlock closed and HTTPS showing on the browser, the HEARTBLEED bug makes it possible for hackers and snoopers to still decipher the encrypted information without the website owners even knowing they were there, if they stole anything or if they are just monitoring the site, using a keystroke logger or employing any number of other ways to snag and store the information on each website.
This is a very slick bug because it is a one way street. The bug can see in, but we can't see the bug or what it is doing until after the fact.
The HEARTBLEED bug leaves no traces of anything abnormal happening to the logs on websites or servers.
It is so very important for each website to install the patch so they are not vulnerable and so they can assure their users that they have their best interests at heart in protecting their private information by upgrading and installing patches, fixes, or install new software to replace questionable software.
This is a good opportunity for affected sites to upgrade security strength of the secret keys they use to safeguard information.
This is a dedicated site where you can read more about AND test your site for safey The HEARTBLEED bug.
How do I know if the HEARTBLEED bug got my information?
If you do any business online, use any website that stores your information, your passwords, your email address, your location and security questions, you are affected! You need to monitor your credit cards and banks for unusual activity.
AFTER all the websites apply the patch to fix their vulnerability, that is when you should change your passwords on each account.
Doing so before then is a waste of time. It will also mean you are giving the bug all your new passwords that you think will safeguard you for the interim until the fix is done. But then you'll just have to do it over again afterward so you have fresh new passwords.
Why is HEARTBLEED not considered a big deal?
To reiterate, The HEARTBLEED bug a bug that breaks down the security of the web encryption program OpenSSL which protects your private information, passwords, email, instant message, bank and credit card information - any information you believe is safeguarded on a site that uses HTTPS (padlock) and promises to store your information.
It is a big deal because if someone steals your personal information, the repercussions can be long reaching into the future, doing irreparable harm to your credit, credit rating, your ability to navigate in this world with your identity which can possibly belong to someone else when they hacked your private information.
Wondering when you should act?
There is no need to wonder.
As soon as you see by the Qualys SSL test (link above) or you get a notice that the websites on the list put in the patch, then it is time to change your passwords on every account you have. Until the patch is in, the website is still not secured.
It is a waste of time to change your passwords now because you will only have to do it again once the website is secure again.
You can also check by clicking this link to monitor CNET's website for updates.
A site to watch for updates
This list is live and going to be constantly updated as sites pass their Qualys SSL Server Test and patch their vulnerable spots. CNET, a major player in determining safe downloads and a dedicated site for up to date news, will maintain the list.
Check in every few hours if any of the sites on the list are your normal hangouts and you will see if their site has done their due diligence to address this awful bug. In the far right column you will see the confirmation from the site and their recommendation.
This is an awful bug, so please keep the site bookmarked, or come back to this hub and it will be updated as CNET is updated.
So if I just wait for sites to fix it, I'm safe, right?
It depends on the website and the website administrators to put the patch in place. Even though the fixed version of OpenSSL is available, they are not ordered or compelled to install the fix.
For example, Yahoo has over 800 million users around the world, but they also control some of the most popular services on the internet that users depend on every day. While they have fixed the top high traffic sites, they still have a long way to go to address all their other website properties, products and services.
See above screenshots for Qualys SSL labs checkup screen.
What you can do to protect yourself, and when to do it
The only way to protect yourself is to change your passwords AFTER the sites apply the patch and to STOP saving your information to servers who promise to safeguard your information.
No matter how easy it is for you to click "REMEMBER ME" or "REMEMBER MY INFORMATION" you do not know who has access to that knowledge - either now or when a breach occurs.
The best thing you can do is what I have been advocating in all the hubs I have written so far about computer technology and that is:
Invest in a little dollar store copybook/notebook and use one page per website to write down your password, your security questions and your sign on information. Put it in a safe place and do not share it with anyone except your immediate survivors so they will be able to access your bank and important information if you should die.
Sites where you can read more about the HEARTBLEED bug
- Internet users told to change passwords
Following the discovery of a major bug known as "Heartbleed," Tumblr has sent out a note encouraging users to change the passwords for all of their online accounts immediately. - Why is it called the HEARTBLEED bug?
It’s called heartbeat because it’s a type of “keep-alive” connection,
Your Opinion Counts
Was any of this information helpful to you?
Don't Copy, Just Spread The Word By Linking. TYVM

© Rachael O'Halloran. April 10, 2014.
No part of this article may be reproduced without prior permission from the author. Use the following link to refer to this article. Do Not Copy. TYVM
http://rachaelohalloran.hubpages.com/hub/Heartbleed-Bug-Leaves-Internet-Users-Open-To-Being-Hacked
© 2014 Rachael O'Halloran