- HubPages»
- Technology»
- Internet & the Web»
- Viruses, Spyware & Internet Security
How To Pick Smart Answers To Your Security Questions
This article will discuss suggestions for answers to password security questions and identity verification security questions, which serve different purposes.
Materials Required To Benefit From This Article
- Pen
- Notebook from the Dollar Store
- An Open Mind
- Common Sense
- A Sense of Humor
Are you giving a hacker the answers to your "identity" security questions?

For online security questions like the ones in the above screenshot ...
Do you lie or do you tell the truth when you give the answer?
Your Passwords Should Be Unique

Password Security Questions
Before I get into how to pick your security questions and answers, I want to get a little housekeeping out of the way and discuss how easy it is for a hacker to learn your password just from your Password Reminder Question.
This question is not the same as your Identity Verification Security Question that verifies your identity. That is a separate screen and usually a different question - or it should be.
Some of this has been covered in my other article about How To Create The Best Passwords Hackers Hate but in case you haven't read that one, this is a little recap.
Password Security Questions are meant to give you a clue as to what you chose as your password. The answer can't be your actual password; it should just steer you in the right direction so you'll remember what the password could be. I like to choose location password answers that have nothing to do with the question, just to tick off a hacker.
Scenario: You are on Site ABC, you already chose a password (with or without using sentence method), and you wrote it down on a page of your Notebook. Now, choose ANY security question - doesn't really matter which one - and make the answer the page number in the Notebook.
Example: Question: What is your the name of your favorite teacher?
Answer: Pagetwoin Notebook (should have a space so it looks like a real name).
Answer translation: Page Two In Notebook - On page two, you should find the password or password sentence you used for that site and the manner in which you wrote it -i.e. the sequence of letters, numbers, symbols, special characters.
If your password is easy for you to remember, then it may be easy for a hacker to get. It is best to make your password so hard that even you have to look it up each time.
- Always use a different password for each site.
- Don't reuse! Passwords should not be recycled.
- Never click SAVE on those "Remember Password" popups. These programs are a gold mine to a hacker.
If you talk, your account walks
If you comment on someone's Facebook page/wall and their settings are set to "public," you have no control. Anyone can read your comments no matter what YOUR settings are set to.
If you talk about your personal stuff - child by name, husband by name, your vacation, upcoming events, etc. - it is all public knowledge.
And you never know who is listening.
Facebook Settings
Your settings on Facebook (and most social networks) where your conversation is in the open for other people to be able to read, should always be set to either "Friends" or "Specifically to certain names." That way, anyone who is not a friend or is not listed on that "specific list" cannot read the conversation. They can't even see it.
If you have no control over the settings, it is assumed that it is all public and anything you say can and will be used against you by a hacker.
Your Facebook Account
You may be wondering why anyone would want to hack your Facebook account since all you do is play games, or talk to friends on your wall, their wall, in groups or chat rooms.
Well, it is not really your Facebook account that a hacker wants.
Hacking into your Facebook account is not the ultimate prize, it is the stepping stone to get to the ultimate prize.
It may be someone on your friends list he has his eye on. You are but a tool - a means to an end.
Your contact (friends) list, your sign-on email address and/or your conversation on your wall or that of your friends is all information he can use to hack other accounts or view any online activity conducted by you or the target.
Remember, even your medical records are online now, (supposedly encrypted, but we all know how that goes!), test results, pharmacy emails, and medical appointments. It is all good information to a hacker in the larger scheme of things.
What he wants is any information that will lead him to guessing your passwords or answers to security questions on all the other sites you use - banks, credit cards, email accounts, blogs, medical records - so he can access them. Once he has them, your identity is his, he can post as you, conduct business as you. He has your whole life. If he can get into your friends list, he has more targets to hack.
Of course, if you are one of those people who uses the same password for two or more accounts, or if you keep an email file with all your passwords on it, then you have helped him immensely.
If you set up your FB account for three attempts, that means when three attempts are made to enter a password without success, the account is locked out to the person doing the attempting! But you are not locked out because you are coming from a different IP address.
An automated email goes to whatever email account you used to sign on, and the email usually asks something inane like "Are you having trouble getting in to your Facebook account?"
A red flag should go up in your mind! Someone's trying to get into your Facebook account and it is not YOU!
Immediately sign on to your account, change the password to something different - use a different sentence - change the sentence to go backwards - anything. Then for peace of mind and possible clue to the culprit, go to SIGN ON ACTIVITY, then view the login activity section to see where the person is located who is trying to get into your account.
Usually it is not a USA city or state, but that's not to say it NEVER is. This information is just some FYI, you can't do anything with it or fix your settings so that someone signing in from Taiwan can't make another attempt.
If this EVER happens to you, you are on someone's radar and need to change your passwords more often than others and be vigilant to those pesky emails from Facebook asking you if you are having trouble getting into your account.
Identity Verification Security Questions
The answer to the Identity Verification Question is meant to verify and to prove to them who you are. The answer must match perfectly, so it is best that the answer be as precise as possible.
Is the answer to your Identity Verification Question so generic that a hacker could guess the answer?
- "In what city were you born?"
- "What is your favorite color?"
- "What is your youngest sister's name?"
As you were reading, did you answer any of those questions truthfully?
Because if you did and if you are hell bent on continuing to answer those questions truthfully, then you are not going to like the rest of this article one little bit.
Let's explore the last question - What is your youngest sister's name?
If you write that her name is Margaret and it really is, what's the matter with you???????
Do you really think the website has to know that????
No.
The website has no idea if her name is Margaret, Cinderella, Wonder Woman, or even Edith Bunker. They don't have any reason to know her name, have no way to verify it, and they don't really care.
The question is being asked so you'll provide an answer and that answer will be "the required answer." It needs to be typed in the answer box in order for them to verify the identity of the person who wants to access the account.
When "the required answer" is typed EXACTLY in the answer box, then that person will gain access to the account. If the hacker doesn't get it exactly right, he doesn't get in.
FunKY LeTTeRinG won't do here.
It is better to be more precise in the answer and leave the funky lettering to some other site that puts more emphasis on it.
If you write some crazy "totally foreign to you" type of name or combination of places or things for your sister's name ... Hooray! You have really pissed off a hacker and kept your account secure.
So ............. Lie.
Lie like a dog.
Then go write it down in your Dollar Store notebook.
Lesson learned: The secret to answering security questions is to LIE.
Get creative in how you answer. Here's another example:
Question: Where did you go on your honeymoon? (Assuming you went to Hawaii, let's use a little "misdirection.")
Answer: aminy
To gain access, a hacker has to know that your abbreviated answer of "aminy" stands for Adirondack Mountains in New York using first letter of each word.
He can keep trying "Hawaii" and other popular honeymoon places until the account is locked out. He won't get your answer if you are creative, precise, yet obscure.
Lie!
Then go write it down in your Dollar Store notebook!
How the 2-step verification process works
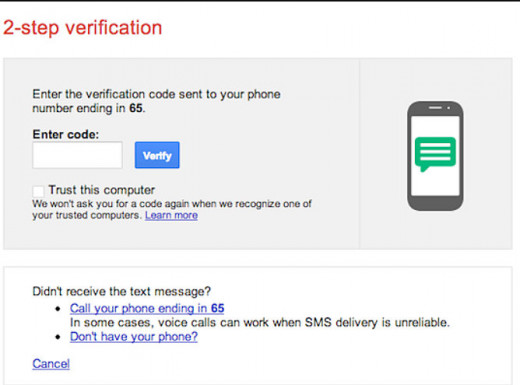
2-Step Verification
If you have a two step verification where a text is sent to your cellphone, it will bypass your email box. Usually security questions are not needed when you have enabled a two-step verification process.
If you don't have a cell phone, you can get a regular phone call where a voice speaks the code to you.
There is no reason to NOT have this level of security. If a site offers it, take it.
Examples Of Challenging Identity Verification Security Questions
What was the happiest day of your life?
- The older you are, the harder this answer is to guess. lol
Give a very obscure answer:
- Notebook page four
- Pick the occasion, make a sentence, then choose ONLY the first letter of each word and add a year for good measure onto the end or the beginning
You have to think like a hacker and then do the opposite. He's trusting that you will tell the truth. Don't.
What is your favorite color?
I absolutely LOVE this question because I can get so much mileage out of the answers.
If your favorite color is purple, for example, don't write purple. Be exact in the color of purple. Magentapurple, Jazzberry, Deepviolet. Choose a purple that has two words, then run them together as I have done. The longer the word, the harder to guess. Don't be afraid to spell them wrong!
If your favorite color is blue, choose a specific color of blue. Morninggloryblue, Cornflowerblue, Bleudefrance, cadetblue, celestialblue. Spell them right, spell them wrong, combine a couple together.
I think you can see how the answers to your favorite color question can be changed so that you almost never have to change the question.
Another common question asks your favorite flavor of ice cream. The hacker is looking for an ice cream flavor, so pick a color instead. Choose an obscure color off the charts at the site linked above.
Write it down in your Dollar Store notebook!

More Ideas
Where did you go to high school?
Instead of giving the name of an actual school, give an intersection address of any high school in your town or the next town. Or give your school colors or your kid's school colors.
- Example: "At Fourth Street and Franklin Boulevard" for the shortened version of At 4th Street and Franklin Blvd that a hacker will use because he is too much in a hurry. Always go long, you aren't crunched for time like a hacker is. lol
- "Katholic" for Catholic, "High Sch" for High School - be misleading by misspelling.
- Burgundyandgold for school colors - all run together as if it was a name of a school
What is the name of the first street you lived on?
I always pick a street in a beautiful neighborhood that I never lived in and then I spell it the wrong way, the short way, the long way or backwards.
- Example: "Secoya Hylands Boulevard" for Sequoia Highland Blvd. OR spell it backwards like this: ayoces sdnalyh draveluoub
- Use up all the space in the box they give you - 32 characters or more
- I used to use "One PoLiCe pLaZa" or "Una polizia Plaza " but they won't accept those anymore because hackers have guessed them to death.
What is your mother's maiden name?
If you actually write down her maiden name, you deserve to be hacked. (joke)
- Don't write the words "mother" or "maiden" - hackers try them first.
- Pick your favorite food, dessert, sport. Capitalize it so it looks like a Proper name. (Examples - Chicken, Gumbo, Tiramsu, Trifle, Ambrosia, Angelfoodcake, Volleyball, Bobsledder)
Write it down in your Dollar Store notebook!
Yahoo's Examples On Video
In the first place, Yahoo wants you to keep it real and answer truthfully with correct spelling. Here's why I think that is a bad idea as well as some of their question choices:
At the 0:52 mark on the video, Yahoo's choice of question: In which city did you study abroad?
This can be a good question for some people, especially those who never studied abroad! But if you actually did take a degree abroad, chances are the school is public record, you are listing the degree and where you got it on your resume on professional sites, like LinkedIn, for example. If you have a professional website where you list your credentials, this is a no-brainer. So, no, I don't think this is a very safe question.
At the 1:11 mark on the video, Yahoo's choice of question: Where did you go on your last vacation?
This is probably one of the worst questions to use as a security question because nearly everyone takes photos on vacation and the likelihood of them being online somewhere, if not in an email to someone, is very high.
When you come home from vacation, you want to post them on your website, Facebook page or send by email to friends or family. You may even talk about it on social media because you are still excited about the vacation. It takes one slip up about this and your security question and answer is blown.
Real Spelling
Where it says in the video to use "real spellings" so you'll remember the security answer, I beg to differ.
If you purposely spell it incorrectly or get creative with spelling, add a number, it makes it that much harder for a hacker to guess.
Remember, it has to match exactly. If you spell it wrong, the hacker has to spell it wrong too!
Stop the video at 0:49 and take a closer look at the security questions they give to choose.
- Who was your date on prom night? Not a bad question -Better, if thename is spelled wrong
- Where did you spend your honeymoon? Choose a sentence, then 1st letter of each word
- Where did you meet your spouse? If it was a city, and especially if it is your present city, it is probably already on social media. If you say BLIND DATE and that is common knowledge, this is not a great security question. Better to choose something like: At Maria's house, or At a convention
- What is your oldest cousin's name? This is a good question -but instead of including the first, middle, maiden and last names, I'd rather pick a nickname. Fat Brucethe Blimp, Twiqqy Jeanthe Stick (Change the G's to Q's)- Make it as hard as possible to guess but write it down so you have it.
- What is your oldest child's nickname? Never a good question, especially if he/she has their own Facebook account and uses the name with their friends
- Name of oldest niece, nephew, favorite aunt, uncle? - all good, but not if you use their real first name, nickname and middle name. Use 3 "words" but never use a maiden or last name. Example: Aunt Alice's son, Uncle Norman's daughter.
- What town was your father (mother) born in? No way, too big a possibility of being public record
Public vs. Private Email Account
Never post your primary email address in public - on a website, Facebook page, in chat rooms, groups, in comments - for people to contact you.
Your primary email address is the private one that has your day to day life in it - for example: business with mail order companies, pharmacy pickup notifications, online payment receipts, credit card statements, bank business, mortgage receipts, any company billing statements, etc.
Instead, always keep at least one backup email address as a secondary email account that is only for your online life - blog comments, HubPages comments or notifications, Facebook groups, playing games, receiving coupons and game bonus offers, etc.
Post that one for people to contact you. If it gets hacked, which is so common now more than ever, at least your financial and private information will be safe in the other account.
Treat the strength of your email account password like it is guarding Fort Knox.
Think about it ... all your important stuff is in there - your communications with your banks, credit cards, sites you do business with, confirmation emails from sites you signed up with - all of these things are what a hacker needs to know so he can start on his merry way going to those sites to hack your password and then get inside the accounts.
Even if you don't think you have anything a hacker would want, you have information that you didn't know you had. Your contact list.
He may not care what stores you shopped at, but your contact list might give him a great choice of friends who do far more on the internet than you do, and who have much more money in the bank than you. And that might be his pot of gold with you being the stepping stone.
Because hackers are guessing the answers, you have to start getting more than just a little creative picking questions and precisely worded answers.
Check out some of my other articles about online safety
- How To Create The Best Passwords Hackers Hate
The dog's name, your favorite color, maiden name. All sound good? Nope-all are guessable! The more creative you are, the harder it is to guess your password. Here's some ways to make great passwords - How Safe And Strong Are Your Passwords?
How safe do you think your passwords are? Pretty safe? Maybe not. Here are ways to protect yourself on and offline. Lists of worse, best & most common passwords. Did your password make the list? - How To Protect Your Credit Before And After A Security Breach or Hack
Security breaches are more prevalent now than ever before. Here's how to protect yourself for FREE before and after a hack or breach. Never pay LifeLock or anyone else. You can do it yourself FREE! - Spotlight On: How Safe Are Your "Electronic Medical Records" From Hackers?
We no sooner have healthcare providers switching everything over to computer databases and now we hear about those very same records getting hacked. Is your physician protecting your info? - Heartbleed Bug Leaves Internet Users Open To Being Hacked
On April 8, 2014,Tumblr announced that internet users were vulnerable to hack attacks by anyone. The padlock is gone and your information is not safe. Here's the lowdown on the HEARTBLEED bug.
Now, go out there and be the best damn liar you can be.
Then go write down your answers in your Dollar Store notebook.
© 2014 Rachael O'Halloran








