78
78- 53
Computer History: Classification of Generations of Computers
This article explains the computer history timeline based on evolving technologies. The 1st had current flowing through vacuum tubes and transistors for the 2nd. The 3rd used IC chips, while the 4th used microprocessor chips. 5th gen computers are meant to be artificially intelligent.
- 5
The Four Types of Computer Software
The four types of computer software include systems, application, malicious and programming software. Computer software, together with hardware and humanware components make up a complete computer system ready for productivity and entertainment.
- 9
The Two Types of Application Software: General Purpose Applications and Custom Software
General purpose application and custom software are the two major types of application software. They are end-user software which contain basic to advanced sets of editing tools. They are designed for productivity, such as arithmetic summation and text editing.
- 94
The Five Types of Systems Software
There are five types of systems software, all designed to control and coordinate the functions of computer hardware. They enable functional interaction between hardware, software and humanware. They are: operating systems, device drivers, firmware, programming language translators and utilities.
- 0
Computer Input-Output Devices
Input output devices are hardware types which deliver both input and output functions.
- 0
Does Activation Lock Bypass By Hermanth Joseph and Benjamin Kunz Really Work?
You probably heard about the IOS exploits of November 2016 which allowed users to bypass Activation lock in iPads. However, questions remain whether the exploits can be used to bypass the iPhone too.
- 0
Anti Static Mat, Wrist Strap and Other Tools That Will Help Safeguard Your Computer From Static Electricity
Anti Static Mat, wrist strap and other protective gear should be priority tools if you plan to work inside the computer. Otherwise, touching the innards of the computer without adequate protection exposes them to immediate or latent damage because of static electricity.
- 1
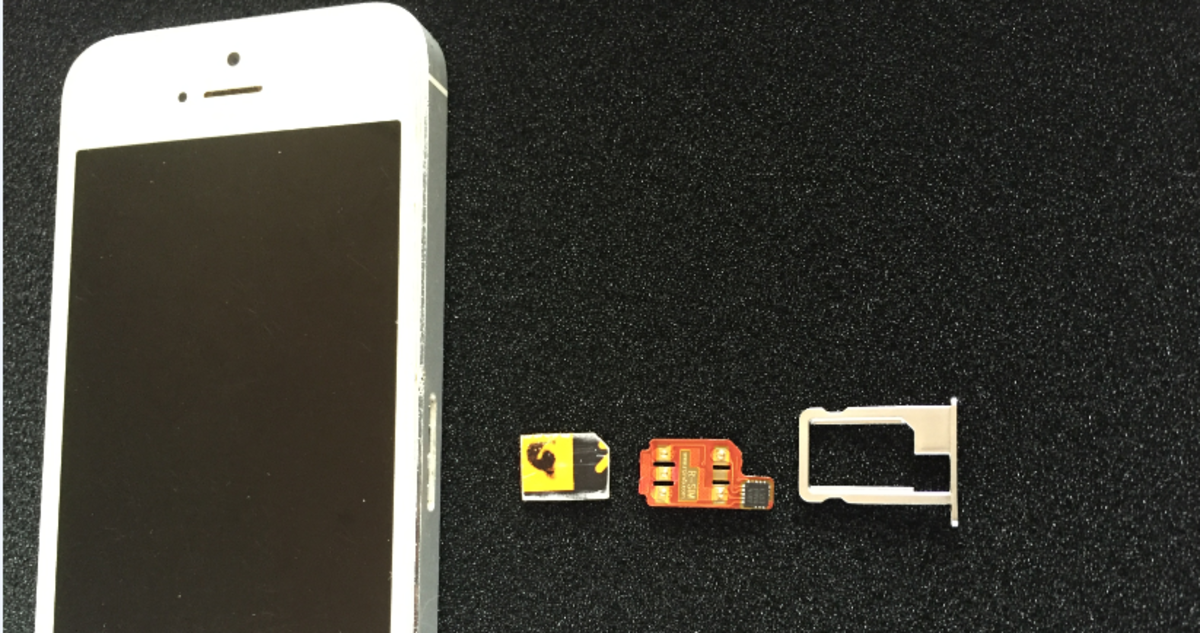
How to Unlock and Activate An iPhone Using R-Sim, X-Sim and Gevey Sim Interposers
In order to activate and unlock the iPhone, the IMEI is usually the best place to start. If, however, the hack does not work, make use of hardware sim interposers like R-sim, x-sim, Gevey sim, GPP and Heicard.
- 0
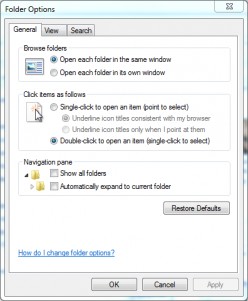
How to Customize File and Folder Options in Windows
You can tweak Folder Options dialog box to index, show hidden files and folders, show file name extensions, switch between icon/thumbnail views, single click to open files and folders etc.
- 1
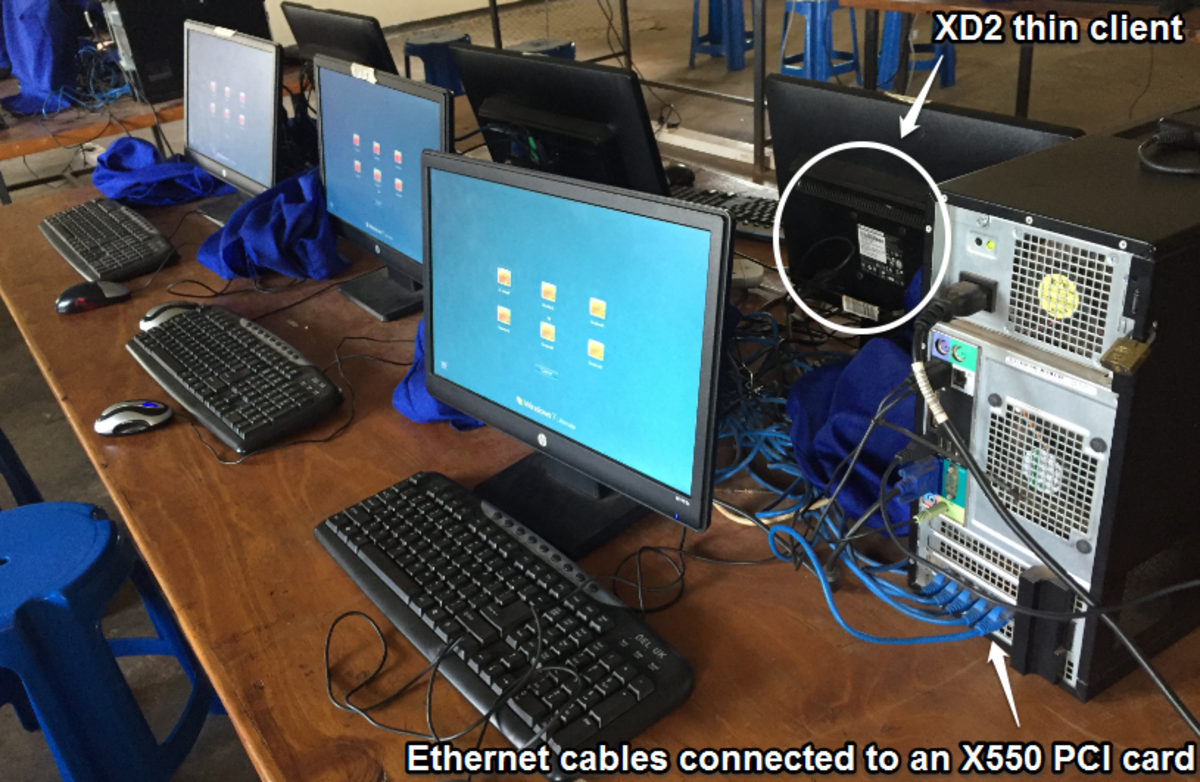
How to Install NComputing X550 Card, XD2 Thin Client and vSpace Virtualization Software
Installation and configuration of NComputing x550 card, XD 2 thin client and vSpace virtualization software allows multiple users to share resources in one host computer using separate monitors and input hardware.
- 0
How to Clean a Laptop Fan and Heat Sink Fins
To clean a laptop fan correctly, eliminating dust bunnies and other dirt in the fan fins and heat sink, you may need a compressed air can or air blower, an airbrush compressor, and a compound like isopropyl alcohol.
- 0
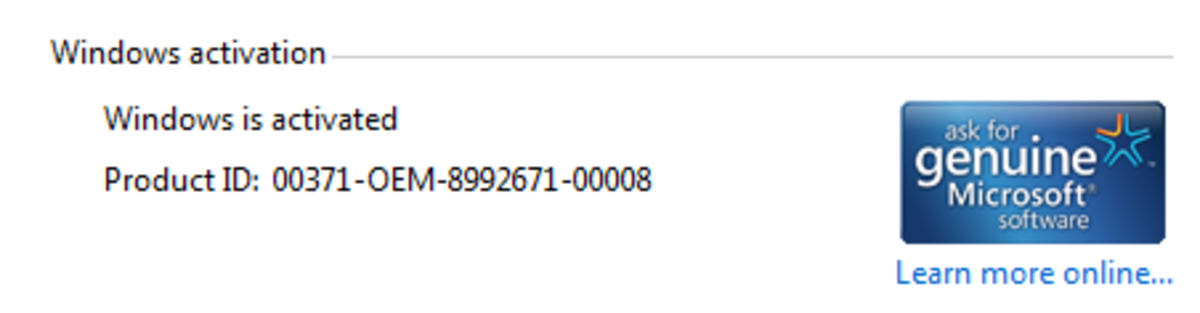
How to Activate Windows 7 & 8 for Free Using Microsoft and Loader/Activator Tools
If you choose to activate Windows installation at home, preferred and optional fixes involve getting help from Microsoft support services and making use of Daz loader/Activator and other pirate tools.
- 0
How to Buy a Used iPhone Without Getting Conned
If you choose to buy a used iPhone, pay close attention to activation and carrier lock status, find out if it is fake or stolen, and of course, do not go for a very old one.
- 12
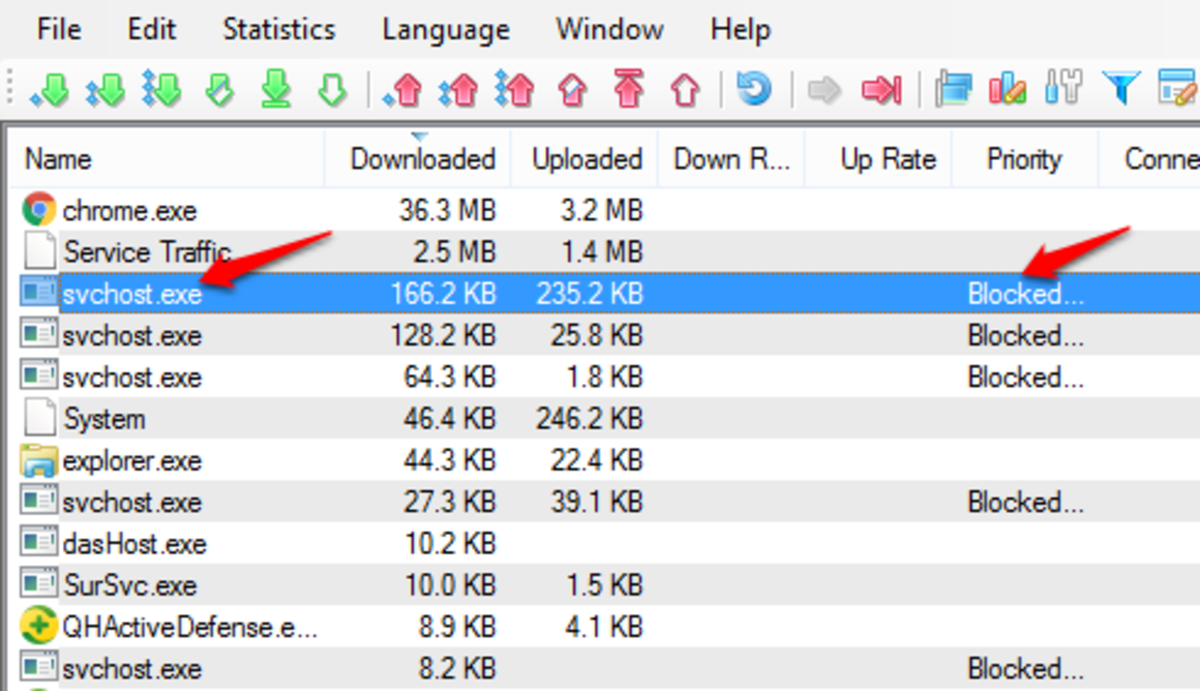
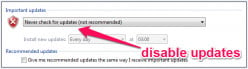
How to Turn off Automatic Updates in Windows
If you make the bold decision to turn off automatic updates for Windows, you have the options to disable related services or use NetBalancer to control and block individual resources.
- 24
20 Common Uses of Computers
From supercomputers to embedded miniature devices, computers can be used to accomplish complex chores like sending man to the outer space or indulging in pastimes like taking photos simply by winking.
- 3
10 Interesting Facts to Expect When You Take a Safari to Uganda, The Pearl of Africa
When you finally decide to take a safari to Uganda, the Pearl of Africa, a few handy facts about its people, cuisine, and lifestyle, may just be what you need firsthand. Then you will have a wonderful safari to a country gifted by nature.
- 2
The Best Computer Virus Protection for the Home User
Cyber attacks and malicious software that we knew a decade ago are a bit of a joke today because of what we now face. Perpetrators are now faster, crafty and extremely destructive demanding for a smarter computer virus protection.
- 2
How to Bypass Windows 7 Password and User Profile Failed the Logon Error
If you wish to bypass Windows 7 password or the 'user profile service failed the logon' error, you can use the Command Prompt or Ophcrack Live CD to recover and access to your PC.
- 6
Classification of Computers by Analog and Digital Signal Processing
Analog signal processing represents data in continuous infinite values. Digital manipulates the same in binary digits. Hybrid uses the best of analog and digital.
- 2
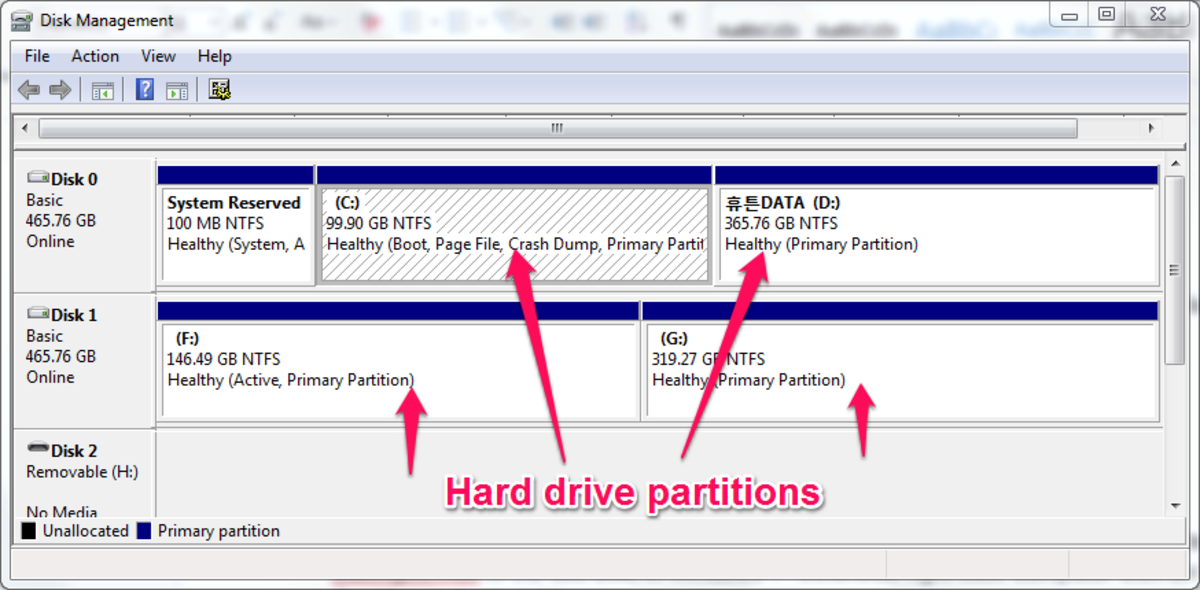
How to Partition Windows Disk Drive Using Windows Setup, Shrink Volume and Easeus Partition Master
You can partition a new disk drive during Windows setup or repartition it using Shrink volume tool in Disk Management and the versatile EASEUS Partition Master.
- 2
DIY Laptop Repair Guide
If you have a little belief inside you, basic laptop repair can be accomplished in the comfort of the sofa without the services of computer repair guy next door. But remember to call him if in doubt!
- 0
Troubleshoot Display Related Faults in Your Laptop
When one morning your display goes black, a number of beep codes and visual signals should guide you to troubleshoot many laptop screen problems.
- 1
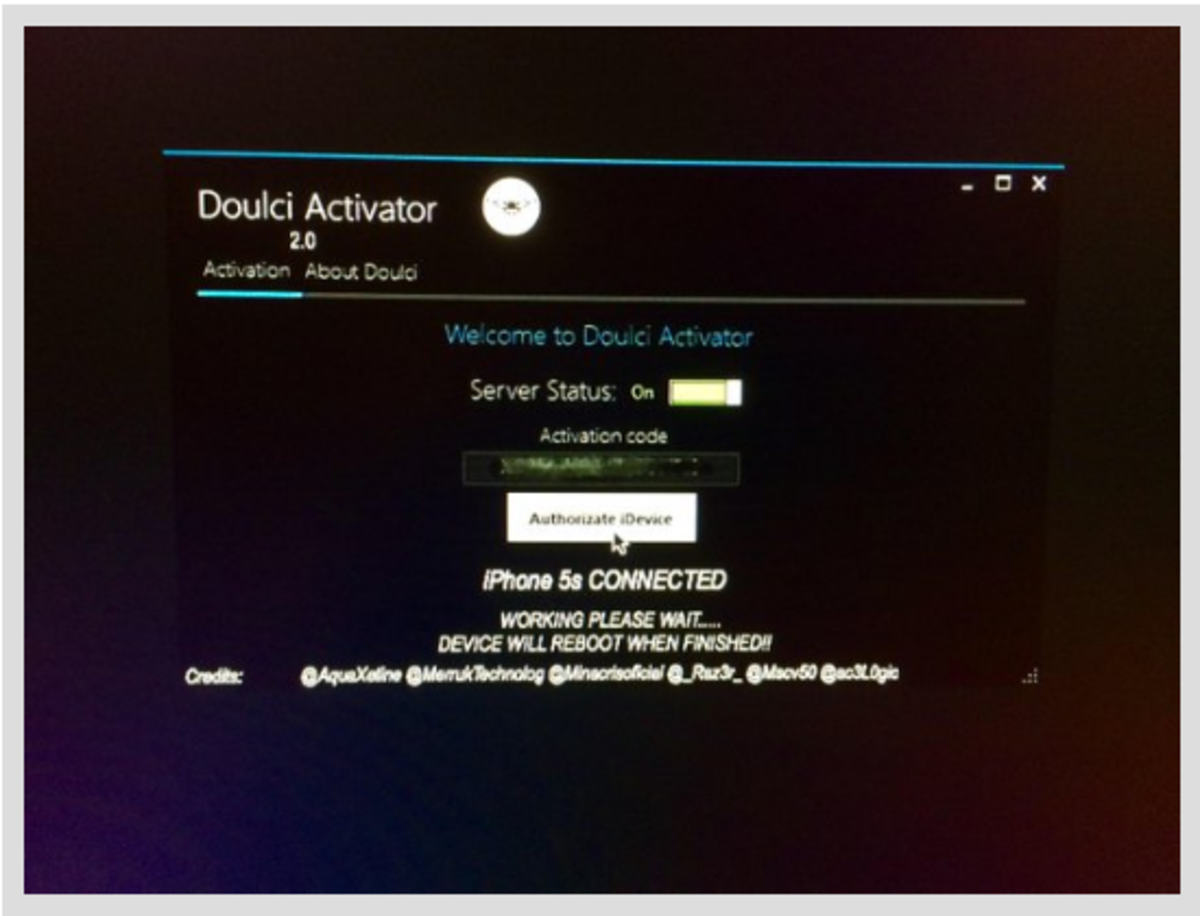
Is it Still Possible to Bypass iCloud Lock Using DoulCi Magic Line?
Fast forward to 2018 and all attempts to bypass iCloud lock seem to have all failed. story. No famed hacker has come up with a legit bypass solution. A host of them have probably given up! and for once, Apple seems to be having an edge over hackers.
- 4
How to Restore iPhone Firmware and Backup
iTunes or a jailbreak tool like Redsnow can be used to restore iPhone firmware. On the other hand, iPhone backup can be restored using iTunes or a third-party application like iTools.
- 3
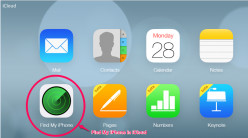
How to Find a Lost iPhone
If you wish to track your lost iPhone, Apple's own Find My iPhone and a host of third party iPhone tracking apps should get you going. While at this, use law enforcement bodies to get the job done.
- 0
Google Glass Use in Medicine, Classroom, Sport and Security
The integration of GPS, gyroscope, Bluetooth, WiFi and camera in Glass opens up a plethora of possibilities which will become important for medicine, classroom and sports and law enforcement.
- 0
How to Download Website Content
There are four popular utilities to download website content for offline reading. They include HTTrack site copier, Scrapbook, IDM Site Grabber and Evernote Web Clipper.
- 2
How to Use Find My iPhone to Protect Your iPhone
Despite doulCi and other hacker exploits, you can still use Find My iPhone and other security features to ensure privacy and protect against iPhone theft.
- 29
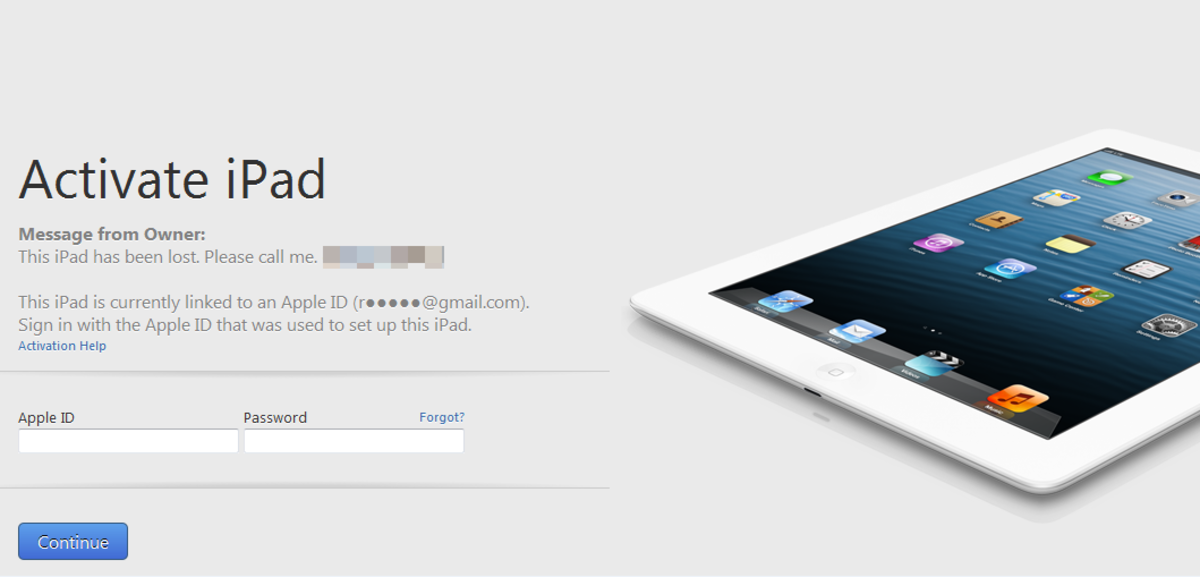
How to Bypass iCloud Lock in iPhone and iPad
It was possible to use doulCi magic lines to bypass iCloud Lock in iPhones and iPads in 2014. The hack has since been replaced by new approaches: You can use the email app to reset the Apple ID, or reset the ID itself, you can contact Enterprise Support, or finally, seek third-party services.
- 2
Symptoms of Hard Disk Drive Failure and Data Protection Strategies
Damage to the hard disk means lost data and memories. For that reason, learn to read into impending hard disk failure. Make use of software utility and implement preventive maintenance.
- 11
Hard Disk Repair at Home
If you decide to do a hard disk repair at home, use the Hard Disk Sentinel utility to confirm its health status before rushing to conclusions. Then you can attempt manual repair hacks by using recovery tools like iCare to get your data back.
- 2
Types of Computer Storage Devices
Computer storage devices can be grouped into two distinct categories: primary memory and secondary memory. While primary memory is volatile and nonvolatile, secondary memory is majorly non-volatile and capable of retaining data for future use.
- 0
Data Processing Devices
Data processing is the core function of the computer, a task which is majorly accomplished by select processing devices such as the central processing unit and graphics processing unit.
- 98
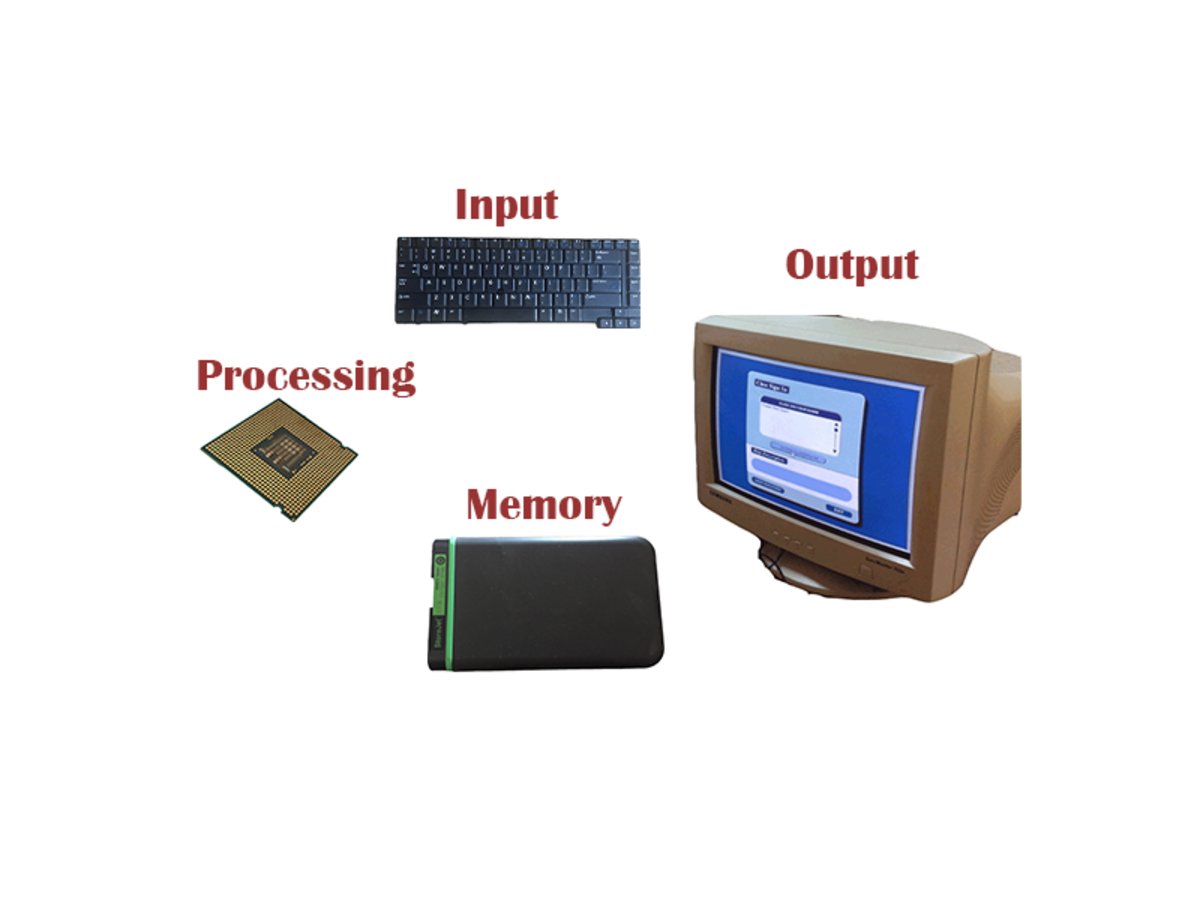
The Four Categories of Computer Hardware
Computer hardware devices are divided into four major categories: input, processing, output, and storage.
- 2
Types of Computer Output Devices
Computer output devices are hardware components that read text, graphics, video, sound, and other digital outputs. The various output forms are transmitted as sound or visual displays and can be saved onto physical storage media.
- 2
Types of Computer Input Devices
Computer input devices facilitate the feeding of data and information into the computer to undergo processing. Examples include keyboard, mouse, microphone and motion sensor.
- 2
How to Control Internet Data Usage at Home
Spikes in internet usage can be a pain if you are unable to find out offending data hogs. But with NetBalaner internet monitoring app and Windows service tool, you should get your data back in check.
- 0
Mobile Money Transfer Spreading From Africa to Europe
When it launched in 2007 in Kenya, mobile money transfer received lukewarm reception. Today, it has become the de-facto means of financial transactions across Africa. Now, it is on its way to Europe.
- 5
iPhone Unlock Using the IMEI Number
iPhone IMEI unlock delivers factory unlock for any iPhone and for any network. Once unlocked using the IMEI, the iPhone will accept SIM cards from all network providers. This can be done through the carrier network reseller or gray market service providers, both for free and for a fee.
- 6
Introduction to Computer Terminology
Computer per se is a very broad subject, and in order to begin grasping its essence, it is best to understand terminology associated with it like Information Age and data vizaviz information.
- 52
Types of Computers: Classification of Computers by Size
Computers are classified into six major categories according to size, with each excelling at specific functions. They are supercomputers, mainframes, minicomputers, servers, personal computers and embedded systems.
- 2
How to Unjailbreak Your iPhone
If you want to unjailbreak your iPhone, you can use iLEX RAT the mobile Terminal from Cydia to do a semi-restore, or iTunes to do a stock restore.
- 2
Apple IOS Security Versus Android Mobile Security
Is Apple account security the safest in mobile? For most the answer would be YES and NO, but in more ways than one, user indulgence rather than OS loopholes contributes to vulnerabilities in Android.
- 4
Causes of Hangover and Its Effects on Your Liver
Hangover is when you indulge in alcohol abuse and wake up feeling like hell. It is made worse by dehydration, bad eating habits, sex type, congener and mixing of alcohol with energy drinks.
- 2
iPhone Jailbreak Using Evasi0n
Evasi0n jailbreak for iPhone 4-5S, brings a new look Cydia app to match the IOS 7. It also comes untethered which means that the iPhone will remain fully jailbroken and functional even after a reboot.
- 0
5 Of The Best Soccer Apps For iPhone And Android
Explained in this article are just 5 popular and free apps available for iPhone and Android users: Eurosport, SkySports, Livescore, Fox Sports and ESPN Sports Center.
- 41
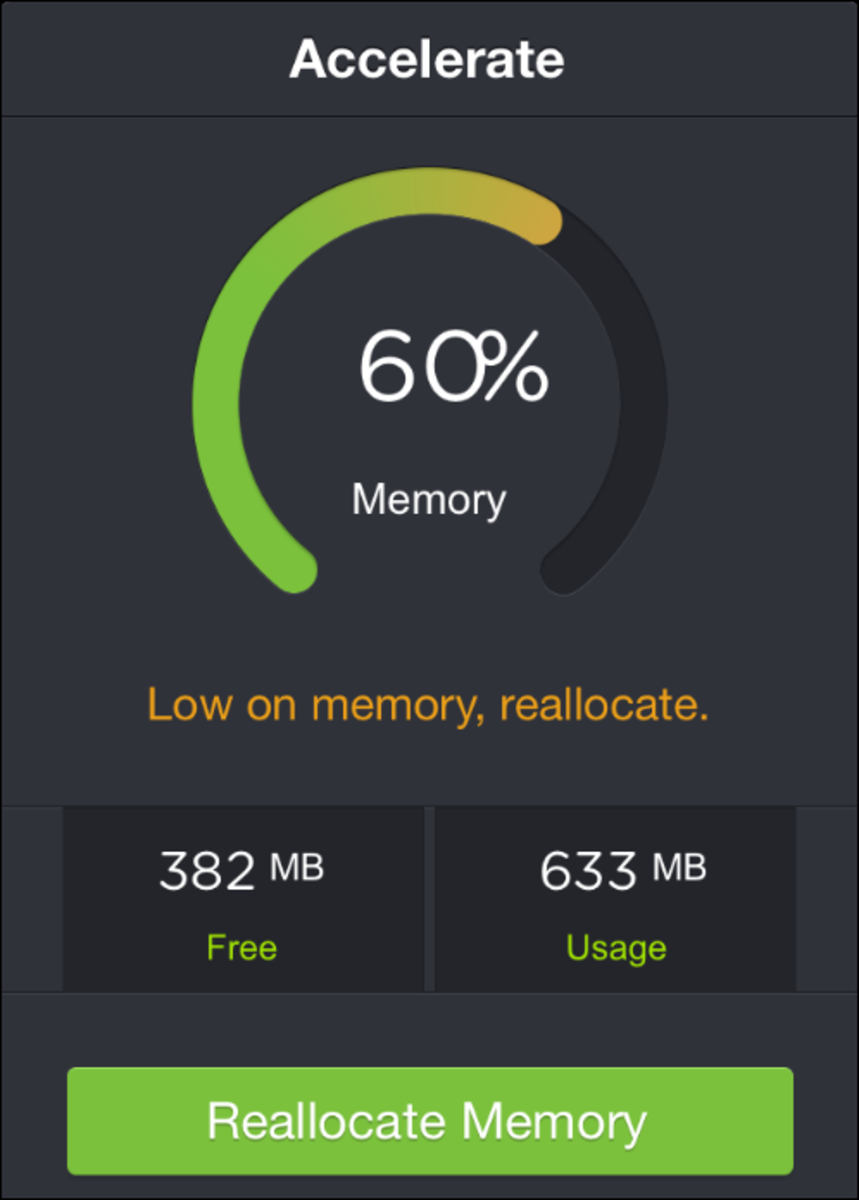
The 4 Functions of a Computer
The functions of a computer include data input, data processing, information output, and data and information storage. Here's what you need to know about each function.
- 11
How to Install Old Version Apps in iPhone 3G and 3GS Using Appsync and iTools
If you wish to install old version apps like Facebook and Whatsapp in your old iPhone, you will first have to jailbreak it, install Appsync 4.X from Cydia and use iTools to install the apps.
- 4
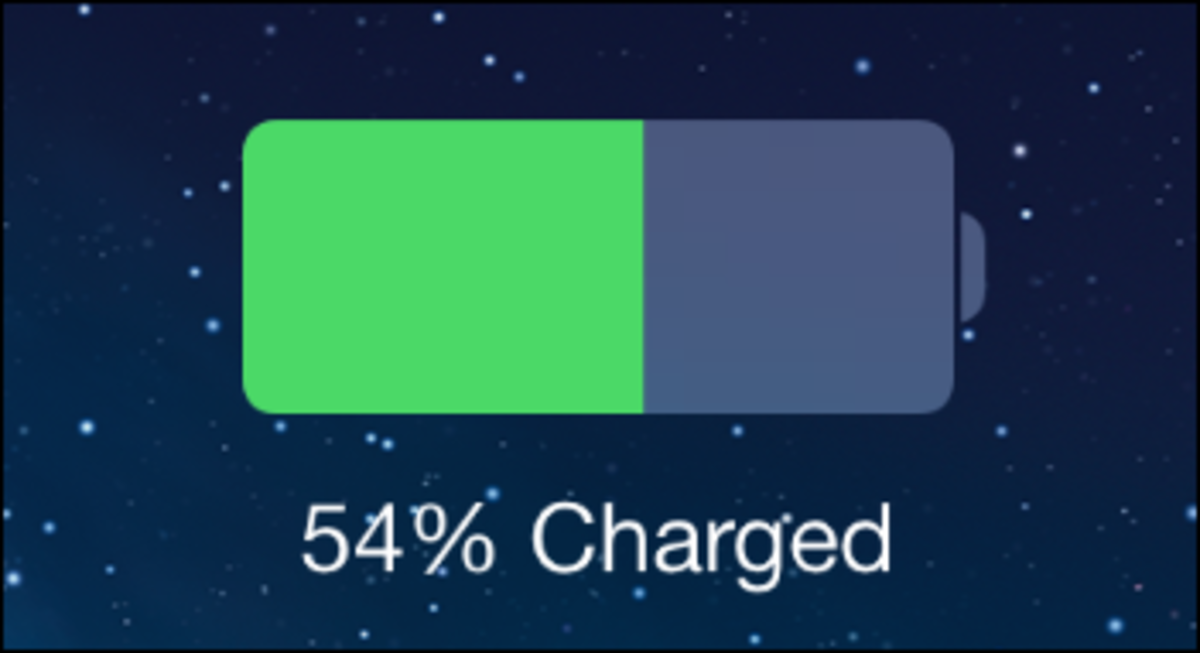
How to Super-Charge Your iPhone Battery
In order to charge the iPhone battery fast, turn your iPhone off while charging, charge via power mains, use genuine charger and turn battery hungry features off.
- 5
iPhone and Android Data and Battery Draining Apps
iPhone and Android data and battery draining apps tend to be the ones used regularly. These are usually apps like Facebook, Google Drive, map apps etc.
- 0
How to Extend iPhone Battery Life
Basic strategies to help extend iPhone battery life include heat reduction, optimizing charge-discharge cycles, and tweaking power hungry apps.
- 3
How to Unlock and Activate an iPhone Using R-Sim 7+, 8+ and 9+
The best way to unlock and activate any iPhone is through use of IMEI request. Other popular procedures to unlock and activate the iPhone includes use of sim card interposers like Gevey and r-sim.
- 9
How to Connect a Computer to a Digital Set Top Box Using the TV Tuner Card
In order to connect a computer to a digital set top box, you will need a TV tuner card installed in a provided PCI card slot. In combination with a digital set-top box you will be able to stream live TV broadcast.
- 0
Transparent Solar Energy and Supercapacitor to Replace Lithium-Ion Battery
The future of mobile battery is transparent solar charging system based on photovoltaic thin film and atoms of graphene oxide additives. Both work with lithium-ion battery to boost energy retention.
- 0
How To Restore iPhone 4 Using Redsnow and shsh Blobs
This article illustrates the instructions used to restore iPhone firmware using Redsnow and shsh blobs saved in Cydia. This procedure means you don't use iTunes at all.
- 0
How to Extend Laptop Battery Life and Avoid Repeated Replacements
If you wish to extend laptop battery life, you need to harness its charge - discharge cycles and battery calibration, only use genuine laptop batteries and adaptors, and of course watch its temp.
- 2
How to Authorize and Deauthorize a Computer with iTunes
If you own an iPhone or iPad you will maximize its usability with online purchases using the Apple ID. You will have to de-authorize old computers and authorize a new one to work well with iTunes.
- 0
How to Put iPhone in DFU Mode
When you put iPhone in DFU mode you place it in pre iBoot state to allow low-level modifications to the iPhone or iPad to take place. The firmware can be upgraded or downgraded. It is a requirement if you intend to upgrade or downgrade the iPhone firmware and baseband.
- 0
How to Set Up Adhoc Network in Windows
Adhoc network is basic wireless networking that facilitates the connection of two or more computers with just a minimum of requirements. At home, it lets you share and print files effortlessly.
- 2
How to Connect Two Computers and Share Files Between Them
In order to share files between two computers, you need to have network capabilities in both computers.
- 2
Why iPhone Jailbreak is Probably Dead
iPhone jailbreak was born out of the desire to exploit IOS to install alternative tweaks and apps. Over time, Apple integrated these into its firmware, and elsewhere, Cydia repositories are closing.
- 0
How to Create a Free Apple ID
An Apple ID account is a requirement if you wish to sync information across your devices, and purchase apps and music from Apple's online Stores
- 2
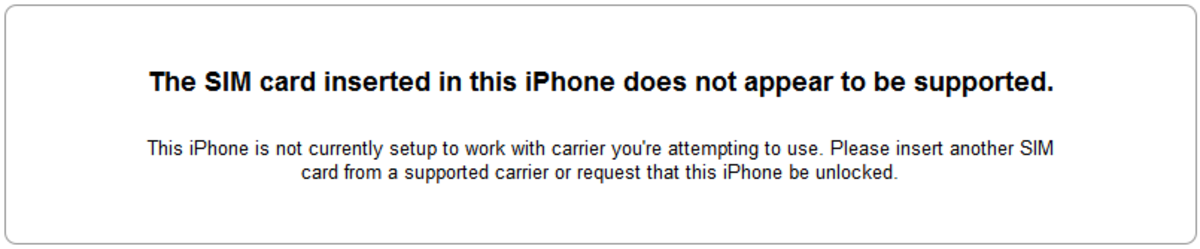
How to Check iPhone Lock Status Using the IMEI Number
If you want to find out the iPhone lock status, the traditional approach involves inserting various sim cards in it and connecting it to iTunes. Alternatively, IMEI.info and iTools can be used.
- 4
How to Buy Durable, Budget, Portable, Business, Gaming and Kids' Laptops
Before you fork out your hard earned money, consider whether it is going to be a budget laptop, a gaming laptop, portable laptop or a laptop for professional work.
- 5
How to Share Files Using Google Drive
Google Drive is a set of web office apps for online file editing, publishing, storage and file sharing.The apps include, Google Docs, Slides, Sheets, Drawing and Forms.
- 39
iPhone Unlock Using Ultrasn0w, Gevey, R-SIM, IMEI Number & SAM
You can get your network provider to unlock your iPhone to factory state using its IMEI number, or seek the services of third party tools like Ultrasn0w, R-Sim and SAM to get partial unlock.
- 0
7 Free and Open Source Software for Windows PC
There is an unlimited collection of free and open source software in the market that should suffice to serve the evergrowing number of users who do not want to purchase off the shelf software.
- 22
New Technology Devices and IT Trends in 2013
If everything goes according to plan, new technology and IT trends in 2013 should help blow our minds away. Apple, Google, Samsung, Microsoft, and Amazon are all determined to innovate in phablets, tablets, smartphones, NFC, voice assistants, smart TVs and mobile devices. While the iPhone 5 is...
- 4
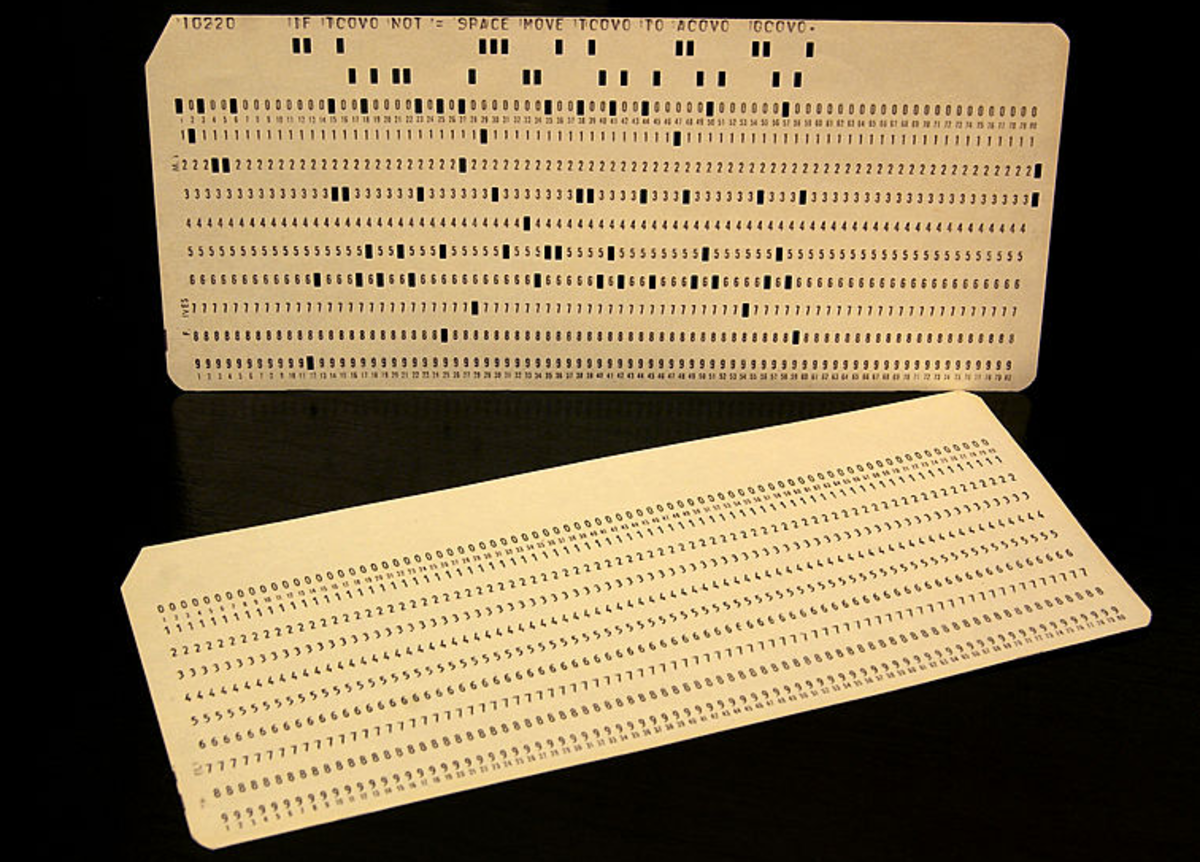
Types of User Interface
The punched card was the first well-known type of user interface. It was faceless and tiresome. Soon, the interaction evolved to command line and graphical user interface. Today, gestures and voice commands are taking over.
- 105
The 3 Major Components of a Computer System
There are three major functions of a computer system: hardware, software, and humanware. Hardware and software exist together to make up the actual computer. The humanware component adds to the life factor to bring the whole computer into a functional existence.
- 5
A Brief History of Computers
Learn all about the history of computers—from the original Z3 to smartphones and tablets—and the innovators who played a role in their development.
- 0
How to Install Windows Drivers Using DriverPack Solution, AIDA and Online Updates
When faced with Windows driver nightmare, you need the following alternative driver installation: Windows driver update, AIDA and DriverPack solution.
- 7
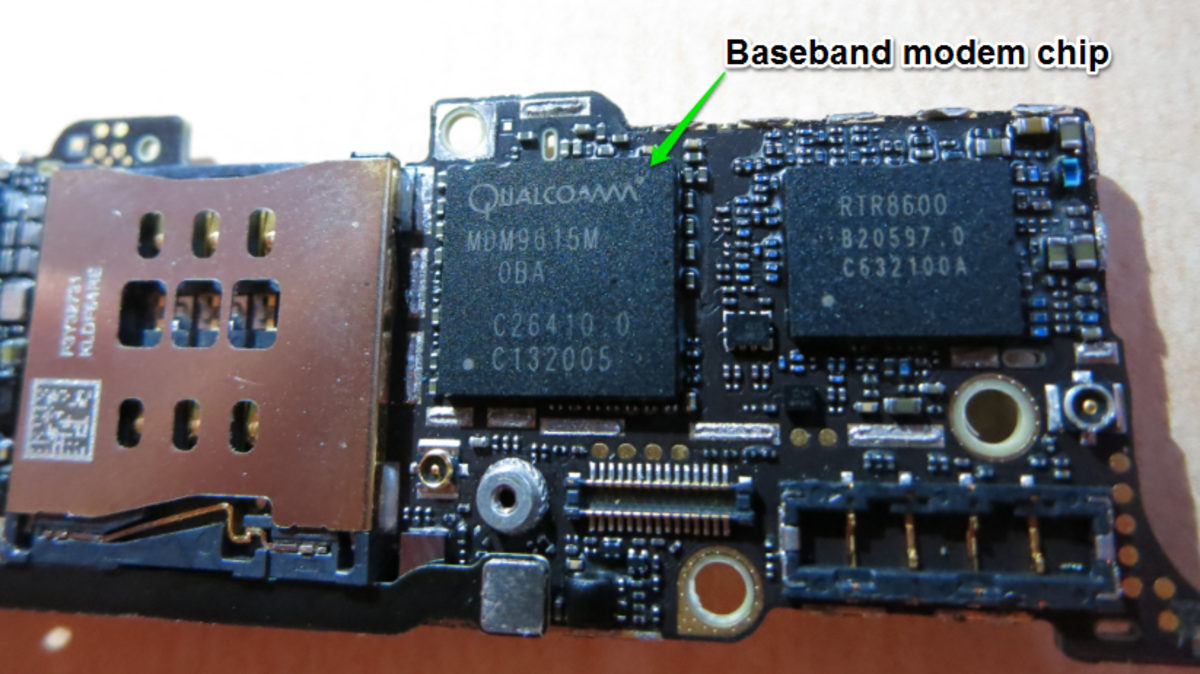
What is iPhone Baseband and Modem Firmware?
iPhone baseband can be explained from both hardware and software perspectives. The hardware component is the modem chip while the software component is called modem firmware
- 3
The Meaning of Windows 7 Activation Crack, Update KB971033 and Windows Genuine Advantage
Windows 7 activation Crack is an exploit into Windows operating system, with the purpose of making it usable free of charge. Microsoft released the infamous update KB971033 to thwart hacker attempts.
- 0
Causes of Teenage Pregnancy
The causes of teenage pregnancy are as diverse, depending on the society and peer influence. With civilization and introduction of education, the case of sexuality changed in many ways. In the years preceding civilization, for example, teenage pregnancy occurred in consensual matrimonial homes.
- 20
What is iPhone Baseband, Sim Lock and Jailbreak?
Get to know what iPhone Baseband, Sim lock status and Jailbreak mean
- 20
How to Use Google Drive in Windows
If you install and use Google Drive in your Windows computer, you will be able to create, edit and collaborate in file processing of Google Docs, Sheets, Slides Forms and Drawing.
- 9
How SAM Exploit Unlocked iPhone 4 Without the Original Sim Card
SAM exploit allowed you to jailbreak and unlock iPhone 4 and 4S. The exploit worked on basebands: 4.11.08 and 4.12.1. It basically worked with IOS 5.