63
63- 1
May be it's love
my love, this is for you ... It's special. It's an unusual feeling. Some distance, closeness.. Keeps my loneliness away Is it love ? Is it trust ? may be It's love ... This is blossoms. This waiting, May be It's love. What to say ?...
- 0
Secure Your Local Data - Offline Protection - 2
Preventing unauthorized users from accessing data means creating a password for everything. You can create a password lock form the very instance your PC starts up by setting a BIOS password. The next step is the operating system for which you can...
- 0
The reason I’m writing a letter is to tell you that I am fine
Many years ago, mills were the only source of income for the people of Mumbai. 250000 labors and relying on them were 600000 people for food. The salary wasn't more but labors were still happy. One day came, which changed the history of Mumbai...
- 3
E Commerce Safety - 1
While e-commerce and m-commerce is on the rise, it is not as popular as it is made out to be among the masses. There is widespread skepticism about the safety of virtual money transactions. Moreover, you don't always end up with the product that you...
- 0
Protect Your Identity on Internet - 1
Your online identity consists of a number of unique details that ideally only you should know. Which some people might think that your name, address, credit card information and account number are the only bits of sensitive information that require...
- 0
Secure Your Local Data - Offline Protection - 1
We store everything, from media to important business documents, on our PCs. So it goes without saying that protecting this data is of utmost importance. One can only imaging the amout of damage done if you lose a hard drive full of local data. ...
- 0
Crack The Code To Data Security
If you are sending across confidential files over email or an external storage device, you can't guarantee that they won't fall into the wrong hands. While password protection is an option, a better way to send these files is ciphering them for...
- 0
Prevent Online Fraud
As the old adage goes, there is no such thing as a free lunch, and so if someone writes you an email saying they want to offer you part of their millions dollar inheritance for a little help from you, then you have every reasons to be suspicious. ...
- 1
The Death of the Netbook
Is there still space in the world for netbooks? Five years ago, the entire world fell in love with the idea of cheap, lightweight computers that could do almost anything. Netbooks shot to the top of the popularity charts so fast that every single PC...
- 0
SMARTPHONE SAFETY - 1
Smartphones these days are capable of doing almost everything a low-end PC can do, which is why the growing number of smartphone users often choose to do their work directly from their phones. The increased activity on smartphones, especially...
- 0
Tweetdeck
Twitter can often be a confusing mess. Once you've started following 10 or more people, it becomes really difficult to keep up with all the updates. The further you scale up, the less practical it becomes to read every single post, and then of...
- 3
TEST YOUR BROWSER SECURITY
There are some websites that can help ensure that your browser settings are optimized for security and are safe from malware.
- 0
Security Analyst: Rising to the Challenge
Security is of utmost importance and often it requires quick thinking and foresight on the part of security professionals, as fast evolving technologies also bring with it newer threats that need to be addressed immediately. A security breach can...
- 0
Secure Browsing
With the advent of cloud computing, on-line shopping, social networking and several other online services, a lot of important information and data is shared over the Internet directly through your Web browser. Add to that the plethora of plug-ins...
- 0
Security Settings for Different Browser
In order to change the security in Internet Explorer, select Tools | Internet Options, and then select the Security tab. Here, you will find a list of security zones for which you can set a specific level of protection. The Internet zone is where...
- 0
Free Phone Management Tool for Android Phone
FOR : Backs up data, file manager and screenshot tool, straightforward UI. AGAINST : Lacks password-protected access. Formerly only for Sony Ericsson cellphones, MyPhoneExplorer now supports all Android phones and tablets. This is by far the...
- 0
Online Shopping Faq
Online shopping is extremely safe and today's consumers are seeing great value in it. Reputed shopping websites offer lots of benefits, such as the convenience of shopping from home, more choice, and easier comparison of prices. Apart from that,...
- 0
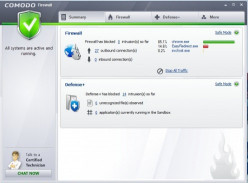
BEEF UP PC SECURITY USING COMODO FIREWALL
If your PC is part of a network that has access to the Internet, malware can spread easily, making your data vulnerable. While you can get applications that govern your Internet usage in parts, a strong firewall application like Comodo helps you...
- 0
Analyzing Software Breakdowns Using Windows Tools
Windows logs everything that happens to it-even software breakdowns. Use this information to find out what is wrong.
- 0
Are Cheap Qwerty Phones Really Good ?
QWERTY phones by big brands like Blackberry, Nokia and Samsung have been around for a very long time. A few years ago, the choices were limited but the market is now flooded with offering by smaller brands like Karbonn, Lava and Micromax, which are...
- 0
ANGRY BIRD MANIA
Pigs may seem like an odd choice of adversary for birds, and you've probably wondered why pigs would steal bird's eggs in the first place. The addition of pigs was apparently inspired by the swine flu epidemic that was rampant at the time when the...
- 2
6D is next to 3D Movies
With the new technology now you will be able to enjoy movies in 6D rather hanging up 3D glasses. This facility is going to be first introduced at The City of Taj, Agra which would be the first such type of theater in Asia and would be opened up by...
- 1
ARE HIGH-END ANDROID PHONES REALLY WORTH IT ?
My journey with Android phone started with the Samsung Galaxy 3, which I've been tinkering with for a long, long time. Initially, it took a little time getting used to the touchscreen, especially while composing emails and message. But after a few...
- 0
Common Admission Test For IIMs
CAT is the entrance exam for the Indian Institute of Management (IIMs) and another approximately 30 management institutes in India. The IIM usually admit about 950 students every year. The other institutes that use CAT for their selection process...
- 2
Get set for the London Olympics
The eyes of the world will be on London on 27 July. The 2012 Olympics Games launch with a fitting showbiz ceremony in the main 80,000-seat stadium, culminating in the lighting of the Olympics cauldron before an anticipated TV audience of four...